Caddy Wiper
File Information
| file Type | PE32 |
| Compiler | Microsoft Visual C/C++ (16.00.30319) [LTCG/C++] |
| Linker | Microsoft Linker (10.00.30319) |
| Tool | Visual Studio (2010) |
| File size | 9.00 KB (9216 bytes) |
| Creation Time | 2022-03-14 07:19:36 UTC |
DsRoleGetPrimaryDomainInformation
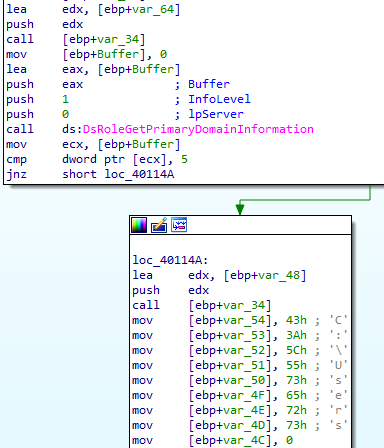
The DsRoleGetPrimaryDomainInformation API is a function in the Windows Server API that provides information about the domain role of a computer in a network. It is part of the Domain Services role services and is primarily used to determine whether the computer is a domain controller, a member of a domain, or a standalone system (workstation or server not joined to a domain).
The DsRoleGetPrimaryDomainInformation function can return different information structures based on the requested information level (InfoLevel). For the information level specified in your example (value 1), the function returns a DSROLE_PRIMARY_DOMAIN_INFO_BASIC structure. This structure contains a MachineRole field which indicates the computer’s role in the network. Possible values for this field are defined in the DSROLE_MACHINE_ROLE enumeration. Here are the typical values you may encounter:
- DsRole_RoleStandaloneWorkstation (0): The computer is a standalone workstation.
- DsRole_RoleMemberWorkstation (1): The computer is a member workstation of a domain.
- DsRole_RoleStandaloneServer (2): The computer is a standalone server.
- DsRole_RoleMemberServer (3): The computer is a member server of a domain.
- DsRole_RoleBackupDomainController (4): The computer is a backup domain controller.
- DsRole_RolePrimaryDomainController (5): The computer is a primary domain controller.
The code compares the obtained value with 5, meaning it checks if the computer is a primary domain controller (DsRole_RolePrimaryDomainController). If the machine’s role corresponds to this value, it means that the computer on which the code is running is the primary domain controller of the domain.
C:\Users directory
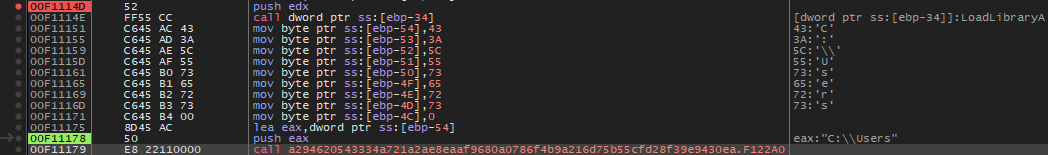
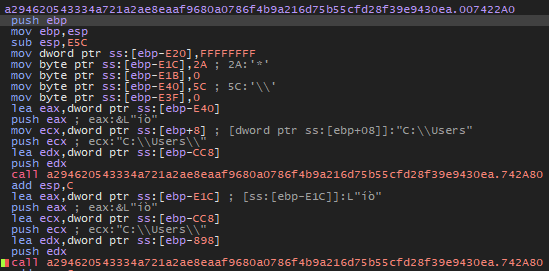
The malware searches for folders at the root of C:\Users.
Loading APIs
Then, the malware retrieves the addresses of the APIs it will use for its operation. First in kernel32.dll, then in advapi32.dll.
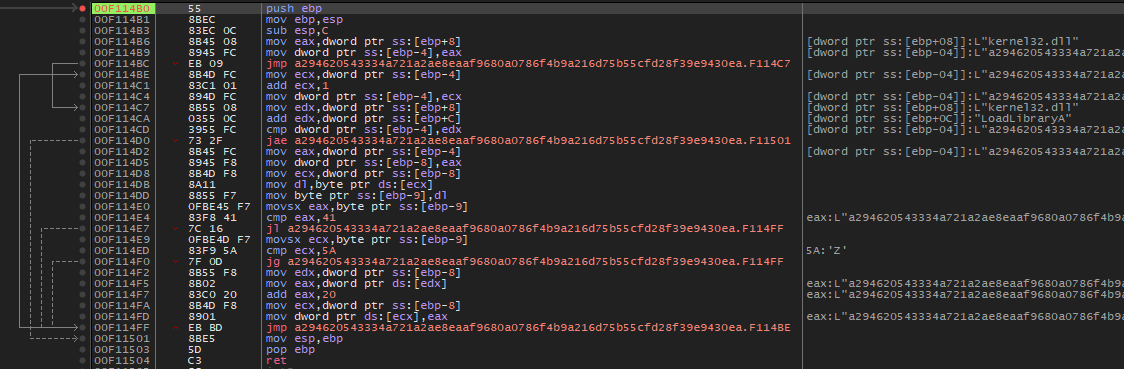
| DLL | API | Function Description |
|---|---|---|
| kernel32.dll | LoadLibraryA | Loads the specified dynamic-link library (DLL) into the address space of the calling process. |
| kernel32.dll | FindFirstFileA | Searches a directory for a file or subdirectory with a name that matches a specific pattern. |
| kernel32.dll | FindNextFileA | Continues a file search from a previous call to the FindFirstFile, FindFirstFileEx, or FindFirstFileTransacted functions. |
| kernel32.dll | CreateFileA | Creates or opens a file, file stream, directory, physical disk, volume, console buffer, tape drive, communications resource, mailslot, or named pipe. |
| kernel32.dll | GetFileSize | Retrieves the size of the specified file, in bytes. |
| kernel32.dll | LocalAlloc | Allocates the specified number of bytes from the heap. |
| kernel32.dll | SetFilePointer | Moves the file pointer of an open file. |
| kernel32.dll | WriteFile | Writes data to the specified file or input/output (I/O) device. |
| kernel32.dll | LocalFree | Frees the specified local memory object and invalidates its handle. |
| kernel32.dll | CloseHandle | Closes an open object handle. |
| kernel32.dll | FindClose | Closes a file search handle opened by the FindFirstFile, FindFirstFileEx, or FindFirstFileTransacted functions. |
| kernel32.dll | GetCurrentProcess | Retrieves a pseudo handle for the current process. |
| kernel32.dll | GetLastError | Retrieves the calling thread’s last-error code value. This function is typically used when a function call returns an error condition and sets the last-error code value. |
| kernel32.dll | DeviceIoControl | Sends a control code directly to a specified device driver, causing the corresponding device to perform the appropriate operation. This is often used for communication with hardware devices and drivers. |
It then obtains the default session folder. It retrieves the addresses of the APIs in advapi32.dll.
| DLL | API | Function Description |
|---|---|---|
| advapi32.dll | SetEntriesInAclA | Sets specified ACEs in an ACL of a security descriptor. |
| advapi32.dll | AllocateAndInitializeSid | Allocates and initializes a security identifier (SID) with specified values. |
| advapi32.dll | SetNamedSecurityInfoA | Sets specified security information in the security descriptor of a specified object. |
| advapi32.dll | OpenProcessToken | Opens the access token associated with a process. |
| advapi32.dll | FreeSid | Frees a security identifier (SID) previously allocated by using the AllocateAndInitializeSid function. |
| advapi32.dll | LookupPrivilegeValueA | Retrieves the locally unique identifier (LUID) used on a specified system to locally represent the specified privilege name. |
| advapi32.dll | AdjustTokenPrivileges | Enables or disables privileges in the specified access token. |
Take the control on User directory
The AllocateAndInitializeSid function is a Windows API function used to allocate and initialize a security identifier (SID), which is a data structure used to represent security identities in the Windows operating system.
SID is a fundamental concept in the Windows security model. It uniquely identifies entities such as users, groups, or computers in a Windows domain. SIDs are used to control access to system resources and determine the permissions that a user or group has on these resources.
The AllocateAndInitializeSid function is used to create a SID by providing information such as the security authority identifier (SID), the sub-authority, and specific user identifier information. Once the SID is successfully allocated and initialized, it can be used in other Windows API functions to perform various access control and security operations.
The SetEntriesInAclA function is another Windows API function used to add or modify entries in an access control list (ACL). An ACL is a data structure that contains a list of access control entries, with each entry specifying the permissions that a user or group has on a particular resource.
The connection between AllocateAndInitializeSid and SetEntriesInAclA lies in the fact that you can use AllocateAndInitializeSid to create a SID representing a user or group, and then use this SID as a parameter in SetEntriesInAclA to define permissions for that user or group in an ACL.
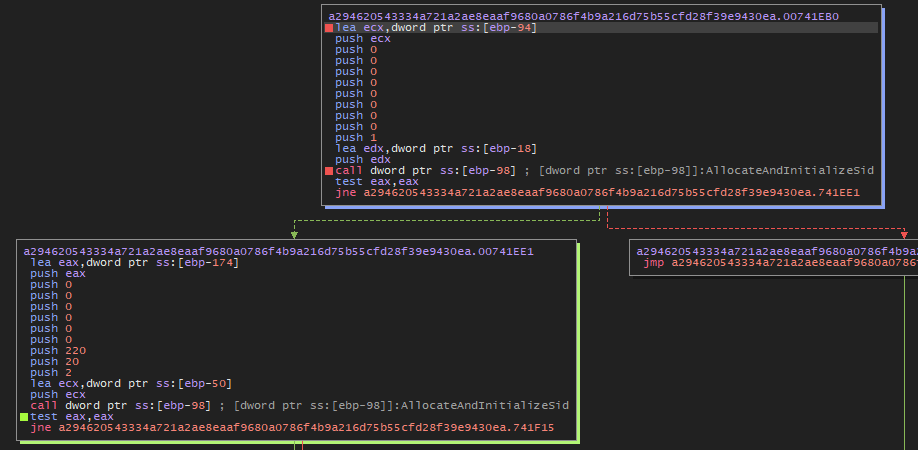
The function SetNamedSecurityInfoA is another Windows API function used to set security information for a named system object, such as a file, directory, or registry key. This security information includes security descriptors (SD), which define access permissions for users and groups.
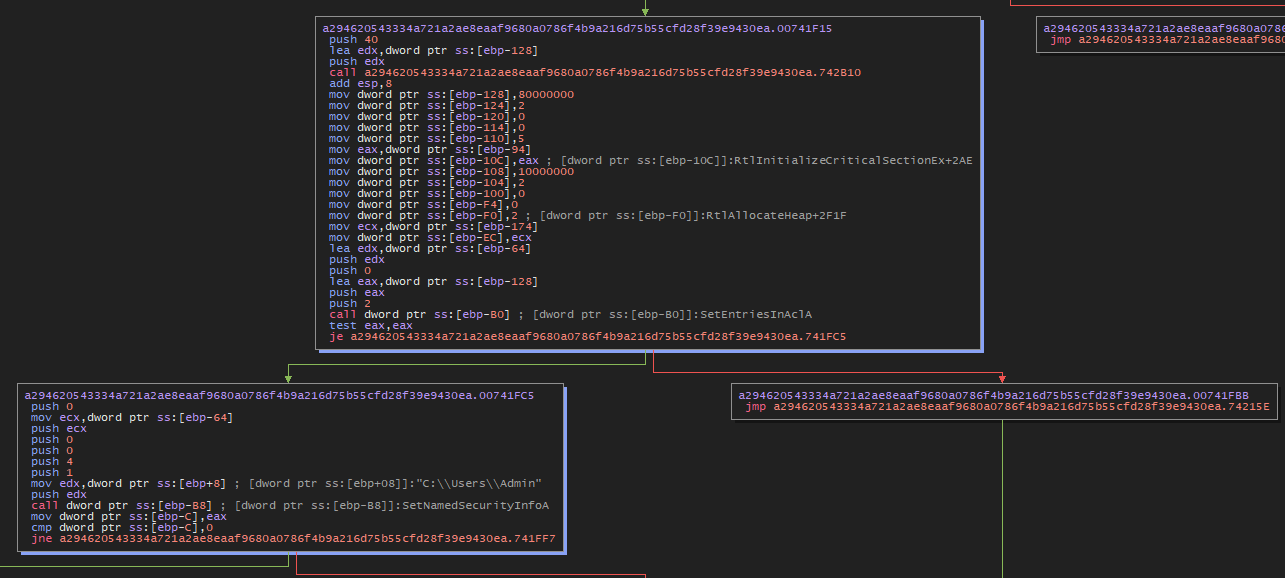
The connection between AllocateAndInitializeSid, SetEntriesInAclA, and SetNamedSecurityInfoA lies in the fact that you can use AllocateAndInitializeSid to create a SID representing a user or group, then use SetEntriesInAclA to define permissions for this SID in an ACL, and finally use SetNamedSecurityInfoA to apply these permissions to a specific system object.
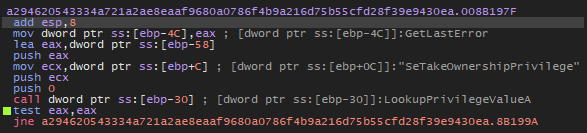
The link between GetLastError, SeTakeOwnershipPrivilege, and LookupPrivilegeValueA lies in the context of error management and security privileges in Windows.
-
GetLastError: This function is used to retrieve the error code of the last failed operation in the calling thread. It is often used after calling a Windows function that may fail, to determine the cause of the failure. -
SeTakeOwnershipPrivilege: This is a security privilege that allows a process to take ownership of any object in the system, regardless of the current access permissions on that object. -
LookupPrivilegeValueA: This function is used to retrieve the locally unique identifier (LUID) associated with a specified privilege name. This allows obtaining the LUID associated with a privilege name, which is necessary for adjusting the privileges of the security token.
The connection between these three functions lies in the fact that when you want to use the SeTakeOwnershipPrivilege privilege to take ownership of an object, you first need to obtain the LUID associated with that privilege using LookupPrivilegeValueA. Then, if the attempt to take ownership fails, GetLastError can be used to obtain information about the cause of the failure, such as whether the absence of the SeTakeOwnershipPrivilege privilege was the reason for the failure.
Take the control on the another disk
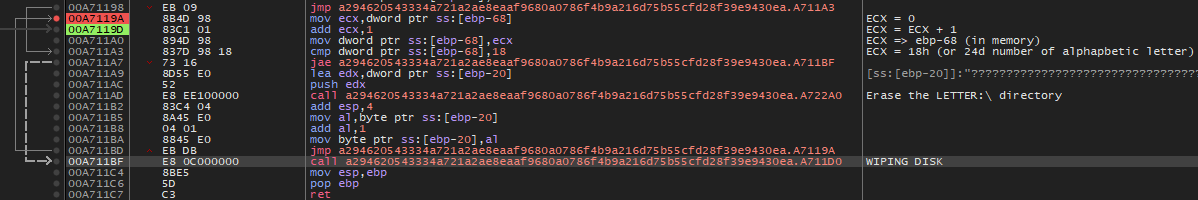
The process used for the folder C:\Users will also be used for the another disk from D:\ to Z:\
Wiping disk
The addresses of the DeviceIoControl, CreateFileW and CloseHandle APIs in the kernel32.dll file will be retrieved.
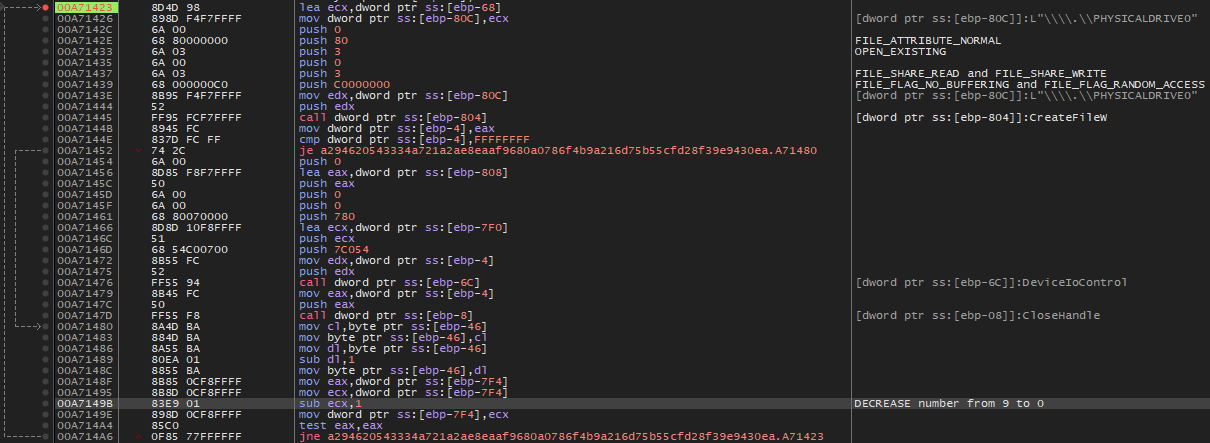
In the context of malware, utilizing the functions CreateFileW, DeviceIoControl, and CloseHandle for the file “.\PHYSICALDRIVE9” could be exploited maliciously to perform unauthorized actions on the physical disk. The process will be carried out on all disks from PHYSICALDRIVE9 to PHYSICALDRIVE0. Here’s how it could work:
-
Initialization of the physical device: The malware uses the
CreateFileWfunction to open the file “.\PHYSICALDRIVE9”, granting it direct access to the system’s physical disk number 9. -
Malicious interactions: Next, the malware uses the
DeviceIoControlfunction to send specific commands to the physical device through the handle obtained withCreateFileW. These commands could include operations such as modifying the boot sector, deleting or altering partitions, writing malicious data to specific sectors, etc. -
Destructive actions or data theft: With direct access to the physical disk, the malware could corrupt the file system, delete partitions, write malicious data to the disk, or even perform formatting operations, resulting in the loss of important data.
-
Covering its tracks: After accomplishing its objectives, the malware uses the
CloseHandlefunction to release the handle of the physical device. This may be done to conceal the malicious activities and make detection more challenging.
In summary, the combined use of these functions allows the malware to perform destructive actions on the physical disk, bypassing the security layers and permissions of the operating system.
Yara Rule
Yara rule are here
rule MAL_WIPER_CaddyWiper_Mar22_1 {
meta:
description = "Detects CaddyWiper malware"
author = "Florian Roth (Nextron Systems)"
reference = "https://twitter.com/ESETresearch/status/1503436420886712321?s=20&t=xh8JK6fEmRIrnqO7Ih_PNg"
date = "2022-03-15"
score = 85
hash1 = "1e87e9b5ee7597bdce796490f3ee09211df48ba1d11f6e2f5b255f05cc0ba176"
hash2 = "a294620543334a721a2ae8eaaf9680a0786f4b9a216d75b55cfd28f39e9430ea"
hash3 = "ea6a416b320f32261da8dafcf2faf088924f99a3a84f7b43b964637ea87aef72"
hash4 = "f1e8844dbfc812d39f369e7670545a29efef6764d673038b1c3edd11561d6902"
id = "83495a0d-a295-5ec7-9761-ce79918e1034"
strings:
$op1 = { ff 55 94 8b 45 fc 50 ff 55 f8 8a 4d ba 88 4d ba 8a 55 ba 80 ea 01 }
$op2 = { 89 45 f4 83 7d f4 00 74 04 eb 47 eb 45 6a 00 8d 95 1c ff ff ff 52 }
$op3 = { 6a 20 6a 02 8d 4d b0 51 ff 95 68 ff ff ff 85 c0 75 0a e9 4e 02 00 00 }
$op4 = { e9 67 01 00 00 83 7d f4 05 74 0a e9 5c 01 00 00 e9 57 01 00 00 8d 45 98 50 6a 20 }
condition:
uint16(0) == 0x5a4d and
filesize < 50KB and 3 of them or all of them
}
Here are the equivalents in the code.
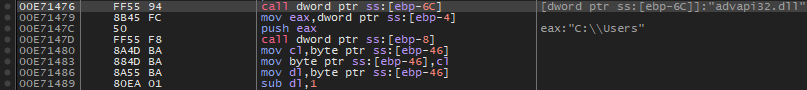
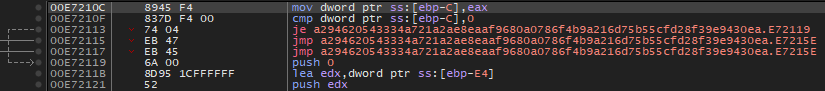
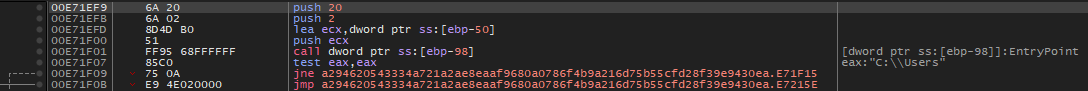
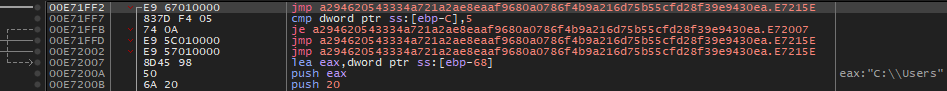
Conclusion
Here comes to an end our article. Caddy Wiper is indeed a devastating malware. Not only does it appropriate privileged rights on the user’s folder, but also on all logical drives of the computer as well as on all physical hard drives.
